geeky stuff
General topics that geeks like.
CarolinaCon – Day 2
0The second day of CarolinaCon was packed from sunup to sundown — who am I kidding… hackers seldom rise before noon. The festivities started at 10am.
Hacking with the iPhone – snide
No, not hacking the iPhone… but using the iPhone as a hacking tool. This talk was a good slide into the morning, a chance to let the coffee sink in. It could probably summarized with two main points:
- Since the iPhone OS is a distant cousin of BSD Unix, many open source (Linux) networking tools can easily be ported to run on it, so a jailbroken iPhone makes a decent platform for network sniffing and the like.
- A jailbroken iPhone provides a behind-the-scenes look at the user interface, and many things that are set on the main GUI can be changed by directly manipulating the underlying settings files.
Neither of these ideas is too surprising, and so this talk was nothing new. Still, for me, having never played with a jailbroken iPhone (honest), it was an eye-opening experience. Or maybe that was just the coffee kicking in.
We Don’t Need No Stinking Badges – Shawn Merdinger
Shawn has spent some time evaluating campus-oriented badge reader door locks from a company called S2 Security. He showed how they work, and how they are advertised to work — not necessarily the same thing. An interesting glimpse into the world of distributed security systems, with several take-home lessons about what not to do.
It’s a Feature, Not a Vulnerability – Deral Heiland
This is the third time that I have seen Deral present at CarolinaCon. In 2009, he showed us what a mistake it can be to “web-enable” your products, and in 2008, he showed us how he made friends at Symantec with “Format String Vulnerabilities 101”.
This time, he continued his endorsement of Symantec’s products by demonstrating how their AMS product conveniently allows very easy access to a machine’s resources. In fact, all it takes is a single packet to tell AMS to run any command on a target Windows box. That’s convenient! (PWNED)
Smart People, Stupid Emails – Margaret McDonald
Margaret came here all the way from Denver to tell us what we already knew… that otherwise intelligent people send the stupidest things in email. This was a lively discussion that we could all relate to… yet I have this sinking feeling that our inboxes will still be filled with garbage when we get back to work on Monday.
Mitigating Attacks with Existing Network Infrastructure – Omar Santos
Omar was cursed with the dreaded 3:00 time slot… just in time for the after-lunch sleepies. It did not help that his presentation was JAM-PACKED with very technical networking information. So, for the most part, I sort of zoned out during this very informative presentation.
I tried hard to stay awake by asking a question (about “bogons” — in this case, the newly-allocated and unfortunately-numbered 1.0.0.0/8 address space). But it did not help.
Omar plans to give this same talk at “Hack in the Box” in Dubai later this year. So if I start feeling regrets that I missed something, I guess I can always book a flight.
OMG, The World Has Come To An End! – Felonious Fish
Hackers are usually prepared for anything… or are they? FF led a discussion on survival, what is needed when the rest of our infrastructure is gone. We might have food and water and shelter, but when my iPhone battery dies, it’s game over!
You Spent All That Money and You Still Got Owned – Joe McCray
Joe’s talk was one of the highlights of the Con… even Stevie Wonder could see that it was awesome. Joe told us his secret to success — he goes into companies, totally pwns them in short order, tells them how they suck, and then they pay him.
Apparently, corporate America makes Joe’s job very easy by following the worst practices. And on the odd chance that they have their operational act together, he can always solicit a security slip-up by sending them a carefully-crafted email (pwn), or if that fails, by leaving a CD with provocative title for some nosy employee to find (serious PWN).
What a life Joe leads — that “education” he got in prison has really paid off.
Locks: Past, Picking and Future – squ33k
The lovely and talented squ33k — 5th grade teacher by day, lock hacker by night — educated us on all things lock-related. With assistance from the TOOOL crew, she taught us how modern pin tumbler locks work, and how they can be picked. But being a full-time teacher, she made sure to frame her talk with some interesting background info on locks from as far back as 4000 years ago, and a glimpse into what locks may be like in the future.
I am so proud that our youngsters are learning their skills and attitudes from this woman. She’s a girl geek role model!
Hacker Trivia
What’s that? Al was spotted in parking lot? Someone allowed him back into the country? I thought that call to the TSA would be enough to keep him detained in the airport until the Con was over. I guess not. HE’S BACK!
Once again, Al Strowger took the stage and led us in a game of Hacker Trivia. Loosely based on Jeopardy!, this game quizzed the inebriated audience on the topics of: Movie Quotes, x86 instructions, other (hacker) conferences, math, 2009 tech, and ccTLD’s. John “Math for 400” Davis took home first prize, an iTunes gift card. Many other contestants won spot-prizes: hacking books, some new geek toys, donated “vintage” equipment, Vic Vandal’s old CarolinaCon 3 t-shirt, and lots of cupcakes.
Good night everybody. Sleep well, we’ll see you at 10am tomorrow morning!
CarolinaCon – Day 1
0It’s that time of year again… time for the annual CarolinaCon security conference. This year promises to be bigger and better than last year — it has expanded from 1.5 days to 2.5 days, and it has moved from the somewhat undistinguished Holiday Inn in Chapel Hill to the somewhat less undistinguished Holiday Inn in Raleigh.
Notably missing was the “Master” of masters of ceremonies, Al Strowger. But Vic Vandal and his cohorts seemed to have the show in order. Personally, I can’t imagine a Con without the provocative charms of Al. But we’ll see how they do.
As usual, the Con started with a short after-work session on Friday night. There were three presentations to get the crowd warmed up.
Cybercrime and the Law Enforcement Response – Thomas Holt, a.k.a. Professor Farnsworth
The good professor never disappoints, and he really had a challenge this time, to warm up an otherwise un-primed crowd. He dove right in, with the not-so-statistically-significant results of a survey of state and local law enforcement officers, asking about their experience with computer crime. It was not surprising to find that most LEO’s were not very well versed in the specifics of computer-based crime, but they had a pretty good appreciation for the concepts. Thank you, CSI. Many trends and prejudices were revealed, and Dr Holt and members of the audience supposed several reasons why these might be so.
The Search for the Ultimate Handcuff Key – Deviant Ollam
If the crowd was not warmed up before Deviant Ollam took the stage, they certainly were after. He and the TOOOL team showed how handcuffs work, and how they can be defeated, sometimes with simple items like a piece of notebook paper!
But just as important as the actual material they presented, was the chosen format of their presentation. In true CarolinaCon fashion, they began by mixing a pitcher of their beverage of choice… tonight’s choice was a “Stone Fence” (one part Apple Jack, three parts hard apple cider, and a splash of bitters). Every time something in their presentation went unexpectedly, they would take a drink — this rule was strictly enforced by the audience.
In case that was not interesting enough, each live demonstration of handcuff picking techniques was accompanied by background music from a famous X-rated movie from the 1970’s and 80’s. In many cases, an audience member was able to “name that movie” before the lock-picker had freed himself, thus winning a prize.
Now this is the CarolinaCon that I came to see.
Microcontrollers 101 – Nick Fury
Finally, Nick showed the audience how to think small… he introduced the AVR microprocessor and the “Arduino” board and tools. Then he showed a few demos of what a small board like that can do. Certainly a tool that many hackers can add to their toolbox.
–
With these three presentations, the Con begins. We’re looking forward to Day 2, which brings a full day of hacking. See you at 10am.
Snakes of a feather
0This time last year, Audrey wrote a computer program in BASIC. Someone had loaned us an Apple II computer, and I showed her what computers were like when I was a kid. I wanted her to write a program, and her mother decided that printing a 10 x 10 multiplication table would be a suitable challenge. So Audrey rose to the task.
This year, I decided to repeat the lesson with Sydney. However, our two girls are very different in personality and interests, and so we had to choose a different approach.
Audrey was motivated by her interest in history, and in learning how Daddy became a nerd. Sydney was motivated by attaching a prize to the assignment — a “feather” on her Indian Princess vest. This would count as one of our father-daughter “crafts”.
I also decided that since I did not have the lead-in of the Apple II computer, I could use any language, and not just BASIC. I went out on a limb and chose Python.
Sydney followed along as we talked about variables and loops, but she was not nearly as engaged as Audrey had been. In her defense, I think the idea of line numbers in BASIC is a little easier for a kid to grasp than the indented blocks of Python. And although formatting the output is easier in Python, all of that punctuation was sure to blow a few fuses in that young mind.
In the end, however, she produced a nice multiplication table.
Here’s her program.
#!/usr/bin/python
import sys
# top line of numbers
print " " ,
x = 1
while x <= 10:
print "%3d" % (x) ,
x = x+1
print ""
# top line of dashes
print " " ,
x = 1
while x <= 10:
print "---" ,
x = x+1
print ""
# ten rows
s = 1
while s <= 10:
# each row is here
print " %2d |" % (s) ,
x = 1
while x <= 10:
print "%3d" % (x*s) ,
x = x+1
print ""
s = s+1
print ""
And here’s what the output looks like:
1 2 3 4 5 6 7 8 9 10
--- --- --- --- --- --- --- --- --- ---
1 | 1 2 3 4 5 6 7 8 9 10
2 | 2 4 6 8 10 12 14 16 18 20
3 | 3 6 9 12 15 18 21 24 27 30
4 | 4 8 12 16 20 24 28 32 36 40
5 | 5 10 15 20 25 30 35 40 45 50
6 | 6 12 18 24 30 36 42 48 54 60
7 | 7 14 21 28 35 42 49 56 63 70
8 | 8 16 24 32 40 48 56 64 72 80
9 | 9 18 27 36 45 54 63 72 81 90
10 | 10 20 30 40 50 60 70 80 90 100
Two days later, Sydney got to show her program to the girls in her Indian Princess tribe. Needless to say, there were some raised eyebrows coming from some of the dads at that meeting.
2009, a year of trying “new things” online
0At the beginning of 2009, I made a New Year’s resolution, of sorts, to try new things online throughout this year. Specifically, I wanted to crawl out of my curmudgeon cave and try new services like online banking — things that had worked “well enough” in my old way, but that might be really cool once I opened up to them. Now that 2009 is over, I would like to report on my findings.
Online Banking
The first area that I wanted to expand my horizons was online banking. This can be a leap of faith, since financial stuff is very important, and since I already had a pretty good system for making sure things got paid on time and for keeping track of finances.
I converted most of my monthly bills into “paperless” billing, and I opened a new bank account that offered a relatively high interest rate in return for being totally paperless. I abandoned my paper filing cabinet in favor of an encrypted thumb drive. I replaced the “bill box” at home with a set of email folders that let me know which bills were in the queue, and which ones had already been paid.
For the most part, this system has worked very well. But there were a few hiccups. For example, one credit card company does not send me an electronic statement if my credit card balance is zero. That makes it hard to tell whether I am paid in full, or if I might have forgotten to download a statement. Also, I do not get email reminders from our city (my last remaining paper bill) when my water/trash bill is due.
Some banks and billers make the process easy, while others stand in your way. For example, my utility (gas and power) bills are sent directly to my bank, where I can pay them. However, to get my credit card company to send their bills directly to my bank, I have to give my bank the login credentials for my credit card company. BUZZ — I don’t play that game. There needs to be some other kind of authorization… like the way that domain transfers are handled, making the request on one side and validating the request on the other side.
There are also some “work flow” glitches. When downloading statements, some banks and billers pop up a “save as” box with a sensible filename filled in, like “Statement-2009-11-05.pdf”. Other billers populate the filename box with something not-so-helpful, like “billdisplay.asp”. Most offer PDF files, but a couple just show you a web page, and it’s up to you to “print to PDF”. I also had to choose how I was going to distinguish between (1) downloaded-but-unpaid, (2) paid-but-not-reconciled, and (3) reconciled bills. Little details like this can make online bill-paying either easy or maddening. But after a month or two, I had developed a new routine that works pretty well.
The one thing I am still getting used to — I end up with a bunch of windows open on the computer: GnuCash, bank web site, biller web site, file browser looking at PDF files, PDF viewer, email client with bill reminders.
Gadgets
I had my eye on the iPhone for a while, and I decided that when my Verizon contract expired, I was going to get one. By chance, I started shopping right as the iPhone 3GS came out, so I snatched one up, and I completely love it. It’s a game changer. It’s the sort of “nerd-vana” always-on network device that I had been wishing Ericsson could develop when I worked there.
A month later, I bought the ultimate iPhone accessory: a Mac Mini. I was hoping to learn how to write applications for the iPhone and iPod Touch. The Apple development tools, of course, run on the Mac.
Social Networking
I have always been a little suspicious of companies like LinkedIn that offer services where you can “build your network” of friends online. It’s just creepy… I feel like I am just feeding the marketing machine.
However, in spite of this, in 2009 I decided to take off all of my clothes and jump into the social networking pool.
I started with Twitter, which immediately appealed to me, with its minimalist design and its non-mutual “following” model. Next came the supposedly-professional LinkedIn and it’s more frivolous (and “fun”) cousin, Facebook. I also experimented with location-based services such as FourSquare and Gowalla, but these did not immediately “stick” with me.
I think the tipping point for me was during our trip to Malaysia. I really enjoyed taking photos with my iPhone and then posting them to Facebook immediately.
Online Services
My paranoia against the gatherers of information extends to the cat-daddy of them all: Google. But this year, I decided that these guys really are offering cool services that I would like to participate in.
So I got a Google Voice phone number, and a Google Wave account.
In 2009, I never got around to posting to Flickr or Youtube, although I had planned to.
Programming Languages
I had been feeling a little stale in my work, so I decided to teach myself a new programming language. I spent a couple of days reading through intro slides to Python, and then I wrote a small program to keep track of a “to do” list. It does not sound like much, but I used this one program as an exercise to learn about model-view-controller architecture, “curses” programming (full-screen windows and boxes on a text-based console), and SQLite (a small embedded database library) as well as the Python language itself.
The staleness at work did not last long. I was asked to help out with a new web application project, so I had to become an instant expert in Javascript and PHP, as well as Zend (a web app framework) and dojo (a set of Javascript widgets that can be used on a web page). Along the way, I also picked up a fair amount of CSS (cascading style sheets, which dictate how a web page is supposed to be laid out on the screen).
Shortly after I bought the iPhone, I wanted to learn how to develop applications for it. So I joined the Apple Developer Program, and I studied Objective C and the Apple development tools (Xcode and Interface Builder) by watching the video courses from Stanford University. After a few weeks, I was ready to write and publish a simple iPhone app called “Tipster”.
New Media
One unintended consequence of getting an iPhone was that I now had a very capable video iPod. So I subscribed to a couple of audio podcasts, so I could have some music to chill to at work.
After a while, I discovered video podcasts as well. I am totally hooked, and I have a backlog of TED.com videos I want to watch.
For fun, Sydney and I produced an audio recording that we referred to as “a podcast”, even though it was delivered to her friends on CD’s. But over the holidays, I decided to learn how to publish a podcast by uploading our audio file to my web server, and then by adding a simple XML index file.
Productivity and Sharing
For years, I have carried a small lab notebook at work. It’s where I keep notes, such as what I did each day, tips and tricks, lab set-up, and administrative details. This year, I replaced my paper lab notebook with a Tiddlywiki, a small one-file wiki that I can carry on a thumb drive. It allows me to easily search for key words, share with others via a web server, and keep multiple copies… and it’s smaller and more durable than my paper notebook, too.
And finally, although I have been publishing the “Porter Family News” every month for ten years now, I decided to supplement it with a WordPress blog. This has been my place to give opinions and observations, and to share tips and tricks with the world.
Overall, I am very pleased with where 2009 has taken me. At times, I had to remind myself to keep an open mind. But I have encountered, and embraced, many changes this year.
Cell phone voice mail “hack” (customization)
3This weekend, I was playing with ring tones, and so I called my iPhone several times to test them out. I started wondering how long it took before my unanswered calls were redirected to voice mail. So I timed it.
By default, it appears that AT&T sets that delay to 25 seconds.
When I worked at Ericsson (1998-2003), I collected a bag of tricks that I used to customize certain features of my phone and my Cingular account. It turns out that some of these tricks still work today. One of those tricks was to set that voice mail delay to a longer value by using the GSM “star” codes.
The wise folks that created the GSM cellular standard understood that some people might have an older phone, but that they might want to use newer network features.
For example, remember the “bag phone” that people used in the early 1990’s? Or the Motorola “brick”? Those had simple calculator-style displays. The did not have a “voice mail” menu… all they could display was numbers! However, the guy at the phone store could program a brick phone to forward unanswered calls to voice mail after a certain delay. Or he could turn on call forwarding. In fact, he is actually telling the BASE STATION to forward unanswered calls, since that’s the piece of equipment that handles that job. After all, the phone itself might be turned off, or have a dead battery, or it might be in Africa somewhere.
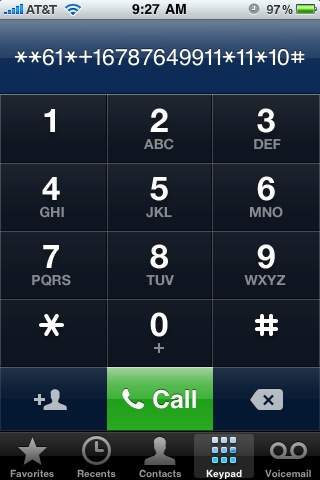
It turns out that most features of the GSM network can be accessed using a series of digits dialed into the keypad. The sequence for call forward on no answer is **61*(target number)*11*(seconds)#.
If you typed that sequence into the old Motorola “brick”, a message would be sent to the base station to say “forward my phone calls to the following number if I do not answer within a certain number of seconds”. That same star code works on a modern phone as well.
This is also how “smart” phones work — the user interface runs on a PDA-like device, and star codes are sent over a serial line to the “GSM modem module”, a completely separate phone-on-a-chip that does nothing but handle the phone calls.
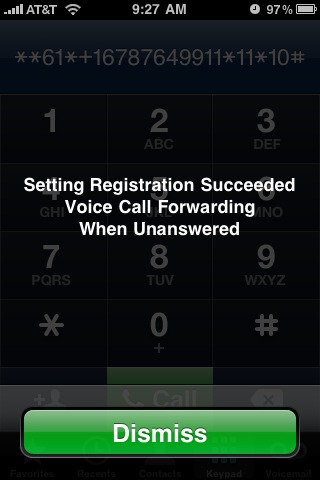
Here’s what it looked like when I customized my voice mail delay from my iPhone. First, I dialed the star code to see what my current voice mail setting was. That code is *#61#.
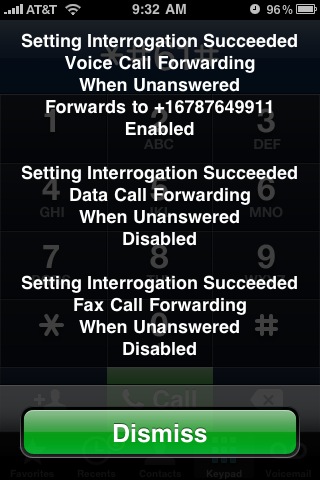
I wrote down the voice mail number — this is the number for AT&T’s voice mail system. Then I dialed **61*+1xxxyyyzzzz*11*10# to see if it would change my “call forward on no answer” delay to 10 seconds.
And I got this confirmation screen.
Then I called my iPhone. Sure enough, after 10 seconds, my call was routed to voice mail.
Of course, 10 seconds is too short — I used that number as a test. So I repeated the process to set the delay to a more reasonable 30 seconds.
A couple of important points:
- This is not hacking. This is a documented feature of GSM cellular networks, and it is exactly what happens behind the scenes when you enter a phone number in the “voice mail” menu of a cellular phone. The only difference is that the menu uses a hard-coded delay value, whereas you can set your own delay if you enter the command manually.
- This process should work on any GSM phone, not just on the iPhone.
Happy @1234567890
0Computers usually tell time by counting the number of seconds since a certain “epoch” time. Then, before displaying the time to you, they do all of the crazy math that defines days of the year and leap years, and even time zones daylight savings time. On Linux systems, the “epoch” is midnight on January 1st, 1970.
At any time, you can tell how many seconds have passed since the epoch by typing:
date +%s
Tonight, at 6:31:30 pm local time, we reached a magic moment when the date was exactly 1234567890 seconds since epoch.
I took this opportunity to show the kids how computers keep track of the time, and to explain time zones (even though they are comfortable with the fact that is it morning in Malaysia when it’s evening here, they did not know about time zones). At the magic moment, we took time out from our pizza supper to watch the time change on my laptop.
Nerds of a feather
0My first exposure to computers was in 1981, when my neighbor “Howdy” (Howard) Petree showed me his family’s TRS-80 Color Computer. His dad gave me some sage advice: “do whatever you want to… you’re not going to break it”. I wrote a simple game called “Al-Zap”, which led the player through a series of scenarios, each followed by three choices: “(1) Eat it, (2) Shoot it, (3) Run away”. I kept the program on three hand-written pages on a note pad, and I manually re-entered it when I wanted to work on it some more.
My interest in computers continued, but I could not go bug Howdy every time I had the urge to tinker. That’s when my friend Greg Reid told me that the public library in downtown Winston-Salem had a lab with four Apple II computers. So my early years of computing were primarily spent hacking on the Apple II’s. Eventually, my dad bought one for our family.
The rest, as they say, is history.
This week, Jeff Mercer from the Triangle Linux User Group offered a working Apple II computer to whoever would come and take it off of his hands. I took Jeff’s offer, and I hooked the old computer up so I could show the girls what “old school” computing was like.
Audrey and I did a little bit of tinkering with Applesoft BASIC, and then I gave her an assignment: to print out a multiplication table. She worked on her FOR/NEXT loops, and soon she had a very nice looking 10×10 table of numbers.
I am very proud of her accomplishment, and even more proud that she took such an interest in her daddy’s past.
Just a sec…
0As we are all counting down to welcome in 2009, we should be reminded to wait just a second, to stop wishing our lives away.
At 7pm Eastern time (midnight UTC), the official international time-keeping standards body inserted a “leap second” into the normal stream of ordinary seconds.
This is done periodically to keep our standard clocks (UTC) in sync with “mean solar time”, which is based on the Earth’s position and rotation. If we did not do that, then Earth-related events such as midnight and noon would gradually shift to different times of the day (likewise, without leap days, the equinoxes and solstices would gradually shift through the year).
At home, I could witness this historic event in the logs of my Linux-based server, bender.
Dec 31 18:59:59 Clock: inserting leap second 23:59:60 UTC
How did YOU spend YOUR leap second?
Segway
0I finally got a chance to ride a Segway.
We spent most of Saturday at the SciWorks museum in Winston-Salem. It’s a pretty cool museum, complete with a planetarium, animal exhibits, and lots of hands-on science exhibits.
While we were milling around, I ran into a guy who looked a little familiar… it was Carl Weston, who used to live down the street from me when I was a kid. He was working at SciWorks, and he was showing people how to ride the Segway. It was a little awkward and slow to get started, but not too hard. I even convinced Foong to take a spin.
By the way, I remember visiting this place about 30 years ago, back when it was called the “Nature Science Center”. Some of the original exhibits are still there, including the Foucault pendulum.
Space shuttle fly-by
0Tonight, we were treated to a visible pass of Space Shuttle Endeavour while it was docked to the International Space Station. On Friday, the girls and I watched the shuttle launch on NASA TV (via internet). So it was pretty cool to see it again, this time live, and in orbit.
