alan
Alan Porter is a mobile application developer, a nerd, a father, and a friend. He is really into gadgets and open source software, and he has spent most of his career making these two things work -- sometimes together. These days, you'll usually find him tinkering with his iPhone. He lives in NC with his lovely Malaysian wife and his two daughters.
Home page: http://alanporter.com
Posts by alan
Misleading VNC Server error – fontPath
0I am working from home today, which involves a combination of working locally on my laptop, but also remotely accessing some resources at the office. My current tool of choice for accessing the PC on my desk is VNC.
A note for Windows users — a VNC server on Windows will share the desktop session that is on your monitor. The default VNC server on Linux does not do this. Instead, it creates a brand new session that is completely independent of what’s on the monitor. If a Linux user wants the same experience that Windows users are used to, he can run “x11vnc”, a VNC server that copies the contents of whatever’s on the monitor and shares that with the remote user.
So when I access my PC remotely, I shell in to my desktop PC and I start a VNC server. I can specify the virtual screen size and depth, which is useful if I want to make it large enough to fill most of my laptop screen, but still leave a margin for stuff like window decorations. The command I use looks like this:
vncserver :1 -depth 32 -geometry 1600x1000 -dpi 96
This morning, when I started my VNC session, it responded with some errors about my fonts. Huh?
Couldn't start Xtightvnc; trying default font path. Please set correct fontPath in the vncserver script. Couldn't start Xtightvnc process. 21/02/12 10:40:55 Xvnc version TightVNC-1.3.9 21/02/12 10:40:55 Copyright (C) 2000-2007 TightVNC Group 21/02/12 10:40:55 Copyright (C) 1999 AT&T Laboratories Cambridge 21/02/12 10:40:55 All Rights Reserved. 21/02/12 10:40:55 See http://www.tightvnc.com/ for information on TightVNC 21/02/12 10:40:55 Desktop name 'X' (chutney:2) 21/02/12 10:40:55 Protocol versions supported: 3.3, 3.7, 3.8, 3.7t, 3.8t 21/02/12 10:40:55 Listening for VNC connections on TCP port 5902 Fatal server error: Couldn't add screen 21/02/12 10:40:56 Xvnc version TightVNC-1.3.9 21/02/12 10:40:56 Copyright (C) 2000-2007 TightVNC Group 21/02/12 10:40:56 Copyright (C) 1999 AT&T Laboratories Cambridge 21/02/12 10:40:56 All Rights Reserved. 21/02/12 10:40:56 See http://www.tightvnc.com/ for information on TightVNC 21/02/12 10:40:56 Desktop name 'X' (chutney:2) 21/02/12 10:40:56 Protocol versions supported: 3.3, 3.7, 3.8, 3.7t, 3.8t 21/02/12 10:40:56 Listening for VNC connections on TCP port 5902 Fatal server error: Couldn't add screen
I scratched around for a while, looking at font settings. Then I tried some experiments. I changed the dimensions from 1600×1000 to 800×600. Suddenly it worked.
Then I noticed that the VNC startup script makes some assumptions. If the VNC server can not start, it assumes that the problem is with the fonts, and it tries again using the default font path. In my case, the VNC server failed because I had specified a large screen (1600x1000x32) and there was already another session on the physical monitor. VNC could not start because it had run out of video memory.
So my solution? I had a choice. I could reduce the size or depth of the virtual screen, or I could kill the existing session that was running on my desktop.
Don’t believe everything you read. That error about the fontPath is misleading. The rest of the error message tells what’s going on. It could not start Xvncserver.
Vacation in Hong Kong, Macau, Malaysia & China
0We try to visit our relatives in Malaysia about every two years. We were due a visit, and so we picked our December/January “track out” (school holiday) to make the trip.
We left right after Christmas, which presents its own challenges. But once we settled into our seats for the 16-hour flight from Detroit to Hong Kong, we left our holiday thoughts at home, and prepared for a whistle-stop tour across Asia.
Hong Kong
Our first stop was Hong Kong, where Foong’s sister Kim lives. Once again, we were impressed with their living quarters, a 700 sq ft 3-bedroom apartment on the 35th floor. Each time I visit, I wonder how I would go about “thinning out” enough to live in a place like that. Foong and I slept on the floor of their office/study/guestroom, with my feet touching one wall and my arm touching the opposite wall over my head. It was a tight squeeze for the two of us. The girls slept in their cousin’s bunk bed.
On Thursday morning, we had breakfast with a friend, Benjamin, who we knew from NC State University. We learned that Benjamin would be book-ending our trip, since he had just gotten a new job in Shanghai, and we would see him again in three weeks. Weird!
We spent most of Thursday touring a small island in Hong Kong called Cheung Chau. Getting there was half of the fun, since we had to go into downtown, and then take a ferry from Victoria Harbor to Cheung Chau. Once on the island, we rented bicycles and explored the beaches, the waterfront shops, and a rocky peninsula that even features a cave tunnel!
Macau
Our visit to Hong Kong was terribly short. On Friday, we boarded a “Turbo Jet” hydrofoil boat that took us to Macao. This weekend get-away was a convergence of three sisters and their families: our family from America, Kim’s family from Hong Kong, and Kit’s family from Shanghai. We spent most of Friday afternoon exploring the old area of town, the ruins of St. Paul’s Cathedral, and a museum of Macau history. That night, we went to the new casino area to see a show called “The House of Dancing Water” (which was remeniscent of shows like Cirque du Soliel). Then we walked around the Venetian Casino, which looks exactly like the one in Las Vegas.
Saturday was New Year’s Eve. Unfortunately, Sydney felt sick, and so she and I stayed in the hotel — she rested and I posted photos to our online photo gallery. Everyone else went to the Macau Tower, a sky-needle-like observation tower. The three kids, Audrey and Emily and John, walked on the “Skywalk”, a platform with no handrail, 764 feet over the city! (They were wearing harnesses). Then they visited a Panda zoo. We met again in the evening, where Foong took over the nurse duty with Sydney, and the rest of us went to downtown Macau for dinner and to see the New Year’s Eve celebration. We returned to the hotel in time to celebrate 2012 together.
Malaysia
On Sunday, said goodbye to Macao and boarded a plane for Malaysia. Thankfully, Sydney was feeling better for the trip. When we arrived, we had some time to relax at our in-laws’ house. In what seems to be the custom whenever I visit, I helped them install a new wireless router (the power lines there are noisy, and they have frequent thunderstorms, and so their electronics devices tend to get zapped fairly often). I set up their new router, and I took a lot of notes, sensing that I might be doing it again on our next visit.
On Monday, we just hung around their home town, Seremban. We had breakfast at their local neighborhood food court, and we visited Foong’s brother’s furniture store. We visited a few stores, but we really didn’t have any shopping to do. We were just soaking the place in.
Tuesday was also a nice quiet day around the house. The girls and I took advantage of the quiet time to read. We did get out a little, to see Foong’s old high school and some stuff downtown. We tried to get the girls to visualize what the town was like when their mother was a young girl.
Tioman Island
On Wednesday, we drove to the eastern shore of Malaysia to catch a ferry to Tioman Island. Tioman is a popular SCUBA destination for Singaporeans — at certain times of year — in December and January, they have strong ocean currents that stir up the water, making it too murky for diving. So this was definitely the off-season, and there were very few visitors. We finally arrived at the Berjaya Resort. The kids were excited because they got their own hotel room (long story).
On Thursday, we hired a driver to take us around the island in his 4WD truck. He drove up a steep and curvy road through the jungle and over the mountain, stopping to show us the sights like some dense jungle and a waterfall. We visited a sea turtle conservatory, and we fed their resident turtle, Jo. On the way back, the girls and I rode in the back of the truck (and I think the driver added a few more MPH to his driving). It was exhilarating. The last stop on our tour was a pier where you could look down on the tropical fish. We wrapped up the day with a swim at the hotel pool and dinner at the open-air restaurant, under the watchful eye of the resident monkeys.
On Friday, we explored the resort a little, and then packed up for the ferry ride back. We drove back to Seremban along some of the most sparsely-populated palm tree plantation land I have seen in Malaysia. In a moment of pure geek pride, I managed to help navigate from the back seat, using my Kindle on the local 3G network and Google Maps.
More Malaysia
Saturday was another stay-at-home day. The kids and I read books and I tinkered on the laptop, while Foong hung around with her sister and brothers. We celebrated Chinese New Year by stirring the traditional “Yusheng” salad, or “prosperity toss”.
On Sunday, we took our teen-aged nieces and nephews to Sunway Lagoon, a water park in Kuala Lumpur. We spent the entire day riding water slides and swimming in wave pools. After the park closed, the teenagers took a train back home, and we visited with several of Foong’s high school classmates who now live in Kuala Lumpur. We spent the night at one friend’s house.
On Monday, we met our niece Josephine, at her office. She works for L’oreal in Kuala Lumpur. It was nice for the girls to see the professional life of their cousin.
Tuesday was our last day in Malaysia, and we basically rested at home… and packed up suitcases… ugh.
Hangzhou
Wednesday started early at the airport. The flight was uneventful, but it took us some time to get oriented after we arrived. To get to town, you can take a bus or a taxi. But there are lots of guys hanging around the airport, offering to drive you around… I chose not to experiment with those guys. We eventually found our hotel near the West Lake of Hangzhou, and we had some time to explore the neighborhood on foot and to find some local food. I also challenged myself to find an electrical converter plug for my laptop — their plugs look like three prongs in a chicken foot pattern. \’/
It was kind of funny… that night and the next morning, the hotel room was very hot. I later learned that the thermostat did not really control anything, but that I could open a window to cool off (it was not obvious that the windows could open).
On Thursday, we walked around the lake area. I quickly decided that I needed to buy some gloves and maybe a hat. I bought gloves, and within 2 minutes of leaving the store, one thumb had started unweaving… Chinese quality! We found a place that rented bikes, and we rode around the lake. It was so cold, we decided to go into a museum to warm up a bit… nope, many public buildings in China are left unheated. It was as cold inside as it was out! That evening, we met two of Foong’s cousins, who are both living in Hangzhou. We saw one cousin’s apartment, and then we went to a very nice shopping mall for dinner.
Shanghai
On Friday, once again, it was time to move on. This time, we went to the train station, one of the busiest places we saw in China. Everyone was going somewhere for Chinese New Year. Fortunately, we found that the crowds thinned out considerably if you paid a little extra for a first class ticket. I suppose you’re paying extra for breathing room. Our train to Shanghai was fast, 300km/h (186mph)! Foong’s sister Kit has a driver who picked us up and brought us back to their palatial western-style home in Pu Dong. We picked up John at his school, a very posh British school. Then we took the kids to an indoor play-place, with slides and climbing areas… a nice way to get re-acquainted and burn off some energy. We had supper at their house.
On Saturday, we went to the 2010 World Expo center, where a couple of the countries’ exhibits remain open. The weather was cold and rainy, so it was hard to get into the proper mood for the Saudi roof-top “oasis” exhibit. From there, we went to a modern mall to warm up and browse and shop a little. I bought some nice sweaters (did you know that Chinese zippers are on the left side?). Dinner was “steamboat”, where each diner has a hot pot of broth, and they pick raw items to boil in their own soup mix.
Sunday’s surprise treat was a visit to the World Chocolate Wonderland, a museum devoted to chocolate. I was struck by the catchy jingle that played continuously in the exhibit hall, like an Asian answer to “It’s a Small World”… it’s still in my head! No trip to China would be complete without some shopping in the flea market stalls of Yuyuan, where you can find a wide assortment of cheap trinkets. It’s like DealExtreme.com, in person — you want a Hello Kitty USB flash drive? We finished off with dinner at a western-style restaurant that specializes in elaborate salads.
Monday was our last full day in China, and we spent the morning getting new eyeglasses. The mall had an entire floor devoted to optical shops, probably a hundred shops! What a bizarre bazaar! After lunch, we accepted the fact that our time in China winding down. We wandered another Chinese mall-of-bargains, wondering if we had any more room left in our suitcases. We bought some trinkets for our friends at home who had been looking after our fish and crab, and Foong found a nifty hard-shell iPad cover with a built-in bluetooth keyboard.
Remember Benjamin, who ate breakfast with us on our first day in Hong Kong? By this time, he had moved to Shanghai to start his new job, and so we invited him over for dinner on our last night in China.
Tuesday was a 36-hour day. Our flight left early, but we headed east while the sun headed west, and we met again in Detroit 13 hours later, but somehow still Tuesday morning. Weird.
–
All in all, it was a fun trip.
This one was different than previous Malaysia visits, because we spent just a couple of days in each place before moving on to the next. It might just be a trick of perspective, but I felt like the more interesting places were the ones that we had the least amount of time in. My favorite place, which I would always like to explore further, was Hong Kong.
The other thing that stands out about this vacation was the three distinct types of weather we encountered. Hong Kong was sunny and cool, Malaysia was just plain hot, and China was cold and wet. That combination made it hard to pack suitcases (and it also explains why Sydney and I have been coughing a lot since we got back). I might’ve enjoyed China more in a warmer season.
Now comes the hard part… returning to the daily grind after a month off. Someone remind me what I was doing before we left!
Chrome and LVM snapshots
0This is crazy.
I was trying to make an LVM snapshot of my home directory, and I kept getting this error:
$ lvcreate -s /dev/vg1/home --name=h2 --size=20G /dev/mapper/vg1-h2: open failed: No such file or directory /dev/vg1/h2: not found: device not cleared Aborting. Failed to wipe snapshot exception store. Unable to deactivate open vg1-h2 (254:12) Unable to deactivate failed new LV. Manual intervention required.
I did some Googling around, and I saw a post from a guy at Red Hat that says this error had to do with “namespaces”. And by the way, Google Chrome uses namespaces, too. Followed by the strangest question…
I see:
“Uevent not generated! Calling udev_complete internally to avoid process lock-up.”
in the log. This looks like a problem we’ve discovered recently. See also:
http://www.redhat.com/archives/dm-devel/2011-August/msg00075.html
That happens when namespaces are in play. This was also found while using the Chrome web browser (which makes use of the namespaces for sandboxing).
Do you use Chrome web browser?
Peter
This makes no sense to me. I am trying to make a disk partition, and my browser is interfering with it?
Sure enough, I exited chrome, and the snapshot worked.
$ lvcreate -s /dev/vg1/home --name=h2 --size=20G Logical volume "h2" created
This is just so weird, I figured I should share it here. Maybe it’ll help if someone else runs across this bug.
Maggie
0 In 1995, I bought a puppy as a present for my wife, who was out of town for a few weeks. I wanted her to have a companion around the house while I was at work or on business trips, someone who could bark and warn her when there were noises in the yard.
In 1995, I bought a puppy as a present for my wife, who was out of town for a few weeks. I wanted her to have a companion around the house while I was at work or on business trips, someone who could bark and warn her when there were noises in the yard.
I named her “Maggie”, and I set out to train her on the basics of living in a house.
When my wife got home, Maggie and I met her at the airport. I was disappointed to learn that she and I did not share the same enthusiasm for pet ownership. Making matters worse, Maggie seemed to be confused about this strange woman who had just shown up and taken all of my attention. This battle lasted for a couple of years. Unfortunately, the house-training exercises also took a couple of years.
Maggie stayed with us, and she eventually learned the difference between carpet and grass. She learned her place in the family. She became a constant companion. She reminded us to go outside and get some fresh air.
She moved with us to new places, including a year and a half in Singapore. She watched as our family grew, and she dutifully accepted her demotion with each new child. She slept on our bed, keeping us warm on cold winter nights, and reminding us not to sleep too late on Saturday mornings. She also kept our kitchen floor clean.
As she got older, she became less interested in fetching tennis balls and going for walks, preferring to stay inside, and enjoying her quality nap time. But every day, when I came into the driveway, she would look out the window to see who it was, and she would greet me as I came inside.
 A few months ago, she started showing the inevitable signs of age. I could sneak in without her hearing me. She sometimes needed help going up and down stairs. She fell off of the bed a couple of times, and so was demoted again — to a floor-sleeper. She started wearing diapers at night.
A few months ago, she started showing the inevitable signs of age. I could sneak in without her hearing me. She sometimes needed help going up and down stairs. She fell off of the bed a couple of times, and so was demoted again — to a floor-sleeper. She started wearing diapers at night.
Shortly after her 16th bithday, Maggie grew weak, not wanting to get up to go outside any more. The vet confirmed that she only had a few more days with us. So I stayed with her at night, comforting her while she slept. And today, I worked from home so I could be next to her. This morning, while I worked, she quietly slipped away.
For 16 years, Maggie was a good dog, a close friend, and an essential member of the family. We are grateful that she chose to stay with us for all of that time. She will be sorely missed by all of us.
More photos of Maggie are in our photo gallery.
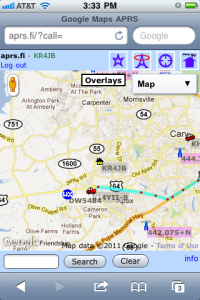
APRS iGate
0When I was working with the NC Nearspace group on our high-altitude balloon, we experimented with two different methods of tracking it once aloft: ham radio APRS, and a commercial system called “SPOT“.
We had some early failures with APRS. But over time, we have found that it’s a pretty nice technology, if you use the proper equipment.
APRS, or “Automatic Packet Reporting System”, is a system that passes data packets over radios. It can be used for passing text messages, but most people use it for telemetry: tracking a vehicle’s position with a GPS, or on a weather station that broadcasts its weather readings every so often.
Since we have been playing with APRS on our balloons, I wanted to learn more about it. I have been keeping my eyes open for a reasonably-priced handheld radio that can encode and decode APRS packets. Sure, some people use a special radio modem (called a “TNC”) to do the encoding/decoding, but it’s important to me to have the modem and the radio in a single package, so I won’t have a big tangle of wires. This week, one such radio popped up on eBay, and so I bought it. While I waited for it to arrive, I did some homework on APRS and what it could do.
Building an iGate at home
I already have two 2-meter radios: a small handheld “handy talkie” and a larger “mobile” radio that is designed to be installed in a car. So I tuned the mobile rig to 144.390 MHz and listened. It was a lot of static, with occasional squawks of data.
Most of the time, if you wanted to decode the squawks, you would buy a packet TNC (modem) to convert the squawks to data, and you’d hook the modem to a computer to use that data. But then I read an article about using your computer’s sound card to encode and decode the packets directly, with no modem at all. Heck, I was sitting around at home waiting for my new handheld-with-built-in-modem to arrive. Why don’t I try to do this modem-less setup?
Look, Ma, no modem!
The first thing I did was hook the speaker output from the radio to my computer’s “audio in”. Optionally, I could have hooked the computer’s “audio out” to the microphone input of the radio. That second step is more complicated than you’d think, because I would also need to hook SOMETHING — maybe a parallel port pin — to the radio’s “push to talk” or “PTT” to turn the transmitter on before it’s ready send a squawk of data over the air. You really don’t want to just let it transmit all of the time… because other people are using that radio channel, too.
I chose the simple receive-only option, setting up my Linux-based server to “listen” to the radio. I downloaded a package called soundmodem, which is a APRS decoder program. It listens to the noise and the squawks, and it outputs a stream of decoded data.
Soundmodem is hard to set up on a headless server, because the normal setup process involves running a graphical configuration program called “soundmodemconfig”. Since my server is “headless”, I don’t have a monitor or a keyboard or a mouse. I just connect to it over the network. So I could not run soundmodemconfig. So instead, I ran this program on my laptop and I copied the resulting configuration file back to the server. It was a pretty simple XML file that looked like this:
/etc/ax25/soundmodem.conf
<?xml version="1.0"?>
<modem>
<configuration name="KISS">
<channel name="Channel 0">
<mod mode="afsk" bps="1200" f0="1200" f1="2200" diffenc="1"/>
<demod mode="afsk" bps="1200" f0="1200" f1="2200" diffdec="1"/>
<pkt mode="KISS" ifname="sm0" file="/dev/soundmodem0" unlink="1"/>
</channel>
<chaccess txdelay="150" slottime="100" ppersist="40" fulldup="0" txtail="10"/>
<audio type="soundcard" device="/dev/dsp1" halfdup="1"/>
<ptt file="none" gpio="0" hamlib_model="" hamlib_params=""/>
</configuration>
</modem>
The important parts are where it says it’ll read the audio device /dev/dsp1 and it’ll create a KISS-mode packet device called /dev/soundmodem0.
To start the APRS decoder program, I just run /usr/sbin/soundmodem /etc/ax25/soundmodem.conf &. If it all works, then I can just do tail -f /dev/soundmodem0 and see some packets on the screen, with some header garbage and then some readable payload data with a bunch of callsigns. That is enough of an indication that the decoding is working correctly.
The iGate software
The second piece of software I installed was a digipeater package called APRS4R. I had read a story about a guy who put a small TNC (radio modem) board inside of a Linksys WRT54G router and turned it into a very small portable digitpeater. He ran APRS4R on the router, and so I figured that this program must be pretty lightweight. So I should be able to run it on my modest Linux server.
APRS4R is written in Ruby (that’s what the “for R” ending means), and it is configured using a single text file. Here is the configuration file that I came up with.
--- !ruby/object:APRS4R::APRS4RConfiguration
version: 1.0.2
devices:
device0: !ruby/object:APRS4R::AX25SocketConfiguration
name: rf0
type: AX25Socket
enable: true
remote:
deprecated:
call: KR4JB
device: /dev/soundmodem0
port:
baudrate: 9600
mode: kiss/tnc2/northlink
speed:
duplicatePeriod: 20
timeout:
parameters: !ruby/object:APRS4R::KISSDeviceConfiguration
name: kiss port
type: KISSDevice
enable: true
remote: false
deprecated: false
device: /dev/soundmodem0
baudrate: 9600
port:
speed: 1200
timeout: 300
txdelay:
persistence:
slottime:
duplex:
device1: !ruby/object:APRS4R::ISSocketConfiguration
name: is0
type: ISSocket
enable: true
remote:
deprecated:
hosts: [third.aprs.net]
port: 14580
username: KR4JB
filter: "# filter m/100"
duplicatePeriod: 20
timeout: 60
plugins:
plugin1: !ruby/object:APRS4R::BeaconPluginConfiguration
name: igate is beacon
type: BeaconPlugin
enable: true
remote:
deprecated:
device: is0
period: 1200
offset: 30
message: !ruby/object:APRS4R::APRSMessage
source: KR4JB
destination: AP4R10
path: []
payload: "!3546.30N/07852.07W-&APRS4R CARY NC"
plugin10: !ruby/object:APRS4R::GatewayPluginConfiguration
name: rf02is0 Gateway
type: GatewayPlugin
enable: true
remote:
deprecated:
call:
inDevice: rf0
outDevice: is0
localOnly:
replacePath:
path:
It’s kind of verbose, but it basically defines two devices called “rf0” (the radio) and “is0” (the internet).
Then it defines a few “plug-ins”, which are actions. I use two actions: a beacon that sends my call letters and position to the APRS internet site, and a gateway that forwards (some) packets from the radio to the internet.
If I had hooked up my radio to transmit as well as receive, then I would have also transmitted a beacon on the rf0 channel, and probably forward some of the incoming internet packets to the radio.
The only tricky bits in this file were:
- For the “is0” destination, I chose a random host from a list that I saw in example files. Mine is “third.aprs.net”.
- The “destination” in the beacon is
AP4R10. That is the code for the APRS4R software package. I have no idea why I send my beacons TO some oddly-named station to signify that I am using this digipeater software package. - The “payload” string in the beacon is
"!3546.30N/07852.07W-APRS4R CARY NC". It consists of a few parts: a bang, my latitude, slash (means “primary icon set”), my longitude, minus (means “house icon” in the primary icon set), and the rest is a comment with my software package name and my location city and state. - I had a hard time choosing which SSID (dash number after my callsign) to use. I finally decided that it does not really matter, because there are several conflicting conventions. But I like using “KR4JB” with no suffix to mean “home”. I will use “-1” for my new handheld and “-2” on the (internet-only) OpenAPRS app my iPhone. If I buy more toys, they will get higher numbers. Balloons typically use “-11”.
Stuff I didn’t do – and why
There were other APRS4R plugins that did stuff like full two-way digipeating and sending beacons on the radio. But my station is a one-way iGate, so I did not need them. My station forwards packets that it hears on the radio to the internet. It does not forward internet packets to the radio.
And my station is not a digipeater, it does not retransmit packets that it has heard on the air.
I run my station as a receive-only iGate for two reasons:
- Most immediately, I did not have a cable to hook into the microphone jack of my mobile radio, and rigging up the PTT looks like a hassle.
- More importantly, you need to coordinate with other digipeaters and gateways around you before you start transmitting packets over the air.
—
This has all been a lot of fun, and I have learned a lot about packet radio. Since I went down a few wrong paths, I learned a lot of stuff that was not immediately applicable. But in this article, I have summarized the parts that got my receive-only iGate working in a single afternoon.
Now I am waiting for my new APRS-capable radio to show up!
Suspend & Hibernate on Dell XPS 15
0In November, I got a new laptop, a Dell XPS 15 (also known as model L501X). It’s a pretty nice laptop, with a very crisp display and some serious horsepower.
I first installed Ubuntu 10.10 on it, and almost everything worked out of the box. But it would not suspend (save to RAM) or hibernate (save to disk) properly. I quickly found a solution to this problem on the internet. It had to do with two drivers that need to be unloaded before suspending/hibernating: the USB3 driver and the Intel “Centrino Advanced-N 6200” wireless a/b/g/n driver.
The solution is to create two files, shown below, that will unload the driver before suspending and reload the driver when it starts back up.
In /etc/pm/config.d/custom-L501X:
# see http://ubuntuforums.org/showthread.php?t=1634301 SUSPEND_MODULES="xhci-hcd iwlagn"
In /etc/pm/sleep.d/20_custom-L501X:
#!/bin/sh
# see http://ubuntuforums.org/showthread.php?t=1634301
case "${1}" in
hibernate|suspend)
echo -n "0000:04:00.0" | tee /sys/bus/pci/drivers/iwlagn/unbind
echo -n "0000:05:00.0" | tee /sys/bus/pci/drivers/xhci_hcd/unbind
;;
resume|thaw)
echo -n "0000:04:00.0" | tee /sys/bus/pci/drivers/iwlagn/bind
echo -n "0000:05:00.0" | tee /sys/bus/pci/drivers/xhci_hcd/bind
;;
esac
A little while later, I “upgraded” to Ubuntu 11.04, but then suspend/hibernate stopped working. Argh!! I tried a lot of work-arounds, but nothing worked.
What’s particularly frustrating about this sort of problem is that you end up finding a lot of posts on forums where some guy posts a very terse statement like “I put ‘foo’ in my /etc/bar and it worked”. So you end up stabbing a lot of configuration settings into a lot of files without actually understanding how any of it works.
From what I can piece together, it looks like the Linux suspend/hibernate process has been handled by several different subsystems over time. These days, it is handled by the “pm-utils” package and the kernel. PM utils figures out what to do, where to save the disk image (your swap partition), and then it tells the kernel to do the work. There are a lot of other packages that are not used any more: uswsusp, s2disk/s2ram, and others (please correct me if I am wrong).
I never really liked what I saw in Ubuntu 11.04, and so I tried a completely new distro, Linux Mint Debian Edition. This distro combines the freshness of the Debian “testing” software repository with the nice desktop integration of Linux Mint. Admittedly, it may be a little too bleeding edge for some, it’s certainly not for everybody. But so far, I like it.
When I first installed LMDE, suspend and hibernate both worked. But then I updated to a newer kernel and it stopped working. So, just like with Ubuntu, something in the more recent kernel changed and that broke suspend/hibernate.
I tried a few experiments. If I left the two custom config files alone, the system would hang while trying to save to RAM or to disk. If I totally removed my custom config files, I could suspend (to RAM), and I could hibernate (to disk), but I could not wake up from hibernating (called “thawing”). I determined through lots of experiments that the USB3 driver no longer needed to be unloaded, but the wireless driver does need to be unloaded.
So with the newer 2.6.39 kernel, the config files change to this, with the xhci_hcd lines removed.
In /etc/pm/config.d/custom-L501X:
SUSPEND_MODULES="iwlagn"
In /etc/pm/sleep.d/20_custom-L501X:
#!/bin/sh
case "${1}" in
hibernate|suspend)
echo -n "0000:04:00.0" | tee /sys/bus/pci/drivers/iwlagn/unbind
;;
resume|thaw)
echo -n "0000:04:00.0" | tee /sys/bus/pci/drivers/iwlagn/bind
;;
esac
At the risk of just saying “I put ‘foo’ in /etc/bar and it worked”, that’s what I did… and it did.
If you have insights on how the overall suspend/hibernate process works, please share. There seems to be a lot of discussion online about particular configuration files and options, but I could not find much info about the overall architecture and the roadmap.
South East Linux Fest
0I enjoyed a “Geekin’ Weekend” at South East Linux Fest in Spartanburg SC.
Four of us from TriLUG (Kevin Otte, Jeff Shornick, Bill Farrow and myself) packed into the minivan and made a road trip down to South Carolina on Friday. We got there in time to see some of the exhibits and a few of the Friday afternoon sessions. There was some light mingling in the evening, and then we all wrapped it up to prepare for the big day ahead.
On Saturday, we had breakfast with Jon “Maddog” Hall before he gave the keynote on how using open source can help create jobs. The day was filled with educational sessions. I attended ones on SELinux, Remote Access and Policy, FreeNAS, Arduino hacking, and Open Source in the greater-than-software world. We wrapped it up with a talk on the many ways that projects can FAIL (from a distro package maintainer’s view). But the night was not over… we partied hard in the hotel lounge, rockin’ to the beats of nerdcore rapper “Dual Core”, and then trying to spend the complimentary drink tickets faster than sponsor Rackspace could purchase them.
Sunday was much slower paced, as many had left for home and many others were sleeping off the funk of the previous night’s party. But if you knew where to be, there were door prizes to be scored. I ended up with a book on Embedded Linux.
It was a memorable weekend, for sure. We learned a lot of new tech tricks, and we enjoyed hanging out with the geeks.
CarolinaCon 7
0CarolinaCon 7
For the fourth year in a row, I treated myself to a weekend of security training and adolescent tom-foolery called “CarolinaCon”. The event was sponsored by the local chapter of 2600. While the presentations covered a range of topics that would interest any security professional, the tone was that of a college party. It’s fun.
The tagline for this year’s event was “A weekend of brainstorming (and by brainstorming, we mean drinking)”.
The Con started on Friday after work, and it continued until supper time on Sunday. While the speakers were giving their presentations in the main room, there were side events going on, too: a “lock pick village”, a weekend-long game of capture-the-flag, and a crypto challenge. It was hard to decide what to do, but I stuck with the presentations.
Here’s my thoughts on the various presentations.
FRIDAY EVENING
- 7pm – Tales from the Crypto (G. Mark Hardy)
Security conferences are known for having puzzle challenges in their admission badges, and Gmark is the twisted mind behind several of them. He gave us an overview of classical (pen-and-paper) cryptography techniques, and showed how these tricks were incorporated into past Con badges. Finally, he issued a challenge to crack the code buried in the CarolinaCon 7 badge. - 8pm – How to Own and Protect Your Office Space (Dr. Tran)
Dr Tran, from the ToooL team (of lock-pickers) showed common weaknesses in office physical security. - 9pm – Serial Killers: USB as an Attack Vector (Nick Fury)
Nick likes to build stuff, and this time he built a small USB device that claims to be a keyboard, or a mouse, or both. And it can type stuff and click on stuff, just like a real mouse. - 10pm – Hacker Trivia (wxs, Vic Vandal, AlStrowger)
Hacker Trivia is CarolinaCon’s version of Jeopardy, where the questions are about hacker topics, and the answers will win you prizes (or crap). I won a lock pick set and a “vintage” (1990) T-shirt that says “Cray Ada 3.0”.
SATURDAY
- 10am – Music and Audio Production with FOSS (Adam Drew)
Some of the audience members partied a little hard last night, so Adam woke them up with some noise/music that he produced using 100% free and open source software. This was my favorite talk of the Con… but it had nothing to do with security. - 11am – PIG: Finding Truffles Without Leaving A Trace (Ryan Linn)
Ryan has given talks before about using metasploit to find vulnerabilities in a network. This time, he showed a plug-in that he calls “PIG”, which does Passive Information Gathering… just listening to what everyone else is willfully broadcasting. - LUNCH BREAK
- 1pm – If You Own a Multi-Function Printer than I Own You (Deral Heiland)
Every year, Deral brings some new way to crack an egg. This time, it was office printers with shoddy security. It’s as if the printer companies got their embedded software guys to do the web interfaces, too! [This, of course, describes MY day job pretty well – I should take notes.] - 2pm – Yara and Python: The Malware Detection Dynamic Duo (mjg = Michael Goffin)
Yara is a tool that can generate a “signature” to help classify malware. I sort of faded out during this one. Hey, it was just after lunch. - 3pm – There’s An App For That: Pentesting Moble (Joe McCray)
We always enjoy seeing Joe Mac, and so we were happy to learn that he could fill a last-minute vacancy with his talk on installing your favorite hacking tools on a mobile phone platform. - 4pm – Fun with SSH Honeypotting (Chris Teodorski)
Best security talk of the Con, starting with a simple tool that looks like a vulnerable SSH shell account, but is really just a frustrating maze that records an intruder’s every move. But not stopping there, Chris went on to profile his intruders by analyzing the rootkit they used, and then by chatting them up in their IRC forum. - DINNER BREAK
- 7pm – Why Your Password Policy Sucks (purehate = Martin Bos)
Using statistics from databases of passwords that have previously been compromised, Martin narrows down the search space significantly, speeding up the time to guess new passwords. For example, a large percentage of passwords are in the form “(some word) + (one number digit)”. Password policies that force you to use a digit only encourage users to choose one that follows this same template. - 8pm – Mackerel: A Progressive School of Cryptographic Thought (Justin Troutman)
There’s a dud at every Con, and this one was it. At first, it looked as though Justin had promise, with his good-ole-boy charm and his trippy slides (done with prezi). But in the end, it was an hour of techno-babble with over-animated slide transitions and no practical substance, a rehash of an academic paper, and a marketing pitch for his consulting business. Boo! [1] - 9pm – TTL of a Penetration (Branson Matheson)
Branson argues that it is more important to react quickly to the inevitable attack than to try to thwart attacks in the first place. Spoken like a real Windows user. - 10pm – Hacker Trivia (Vic Vandal, wxs, AlStrowger)
The Saturday night episode of Hacker Trivia was a little harder-edged than Friday night’s game. The staff spent much more of their time enforcing (and changing) the rules, and generally arguing with each other. Al (the MC) commented that this was like a game of “CalvinBall”. The cheezy prizes were replaced by unique “CarolinaCon 7” shot glasses, awarded (full) to the correct answerers.
SUNDAY
- 10am – logstash: Open Source Log and Event Management (Jordan Sissel)
Most of us just print logs to a file. Jordan Sissel manages logs like Sorcerer Mickey manages his broom minions. His open source tools consolidate, format and distribute log messages in a very flexible way. And he even has stickers with cartoon logs and beavers to boot! - 11am – Dissecting the Hack: Malware Analysis 101 (Gerry Brunelle)
When a machine is hacked, many people want to just wipe it clean and reinstall the OS. Gerry tells us not to… save that image and study what the malware is doing. He showed several techniques for learning what a piece of malware is doing. This was primarily a Windows-based talk, and much of the work was done using debuggers that disassembled the object code. - LUNCH BREAK
- 1pm – Security Lessons from Cracking Enigma (Lisa Lorenzin)
Lisa walked us through the history of the German Enigma machine, and the extraordinary tale of how the code was broken by the British and the Allies. - 2pm – Hack from a Library with Katana (JP “ronin” Dunning)
A pretty straightforward talk about a toolkit that can be installed on a USB flash drive, and about the many places where one might find an unattended PC (McDonald’s drive-thru??). - 3pm – The Art of (Cyber) War (wxs = Wes Shields)
It’s time to put on our tin foil hats… Wes is about to tell us about the next generation of bad guys. While the media warns us of APT’s (Advanced Persistent Threats), Wes prefers to call them DHA’s (Determined Human Adversaries). They are organized, focused, funded, and take a long-term view of their attack. So determine what their motivation is, and how to counter them. Apologies for numerous Sun Tsu quotes. - 4pm – Pwning Capture the Flag: Step by Step (David Burt)
David Burt set up the playing field for the weekend-long capture-the-flag game, and so as the Con came to a close, he spilled the beans. Five machines were set up on a private network, two Linux machines and three Windows. Each had vulnerabilities and “flag files” hidden on them. Find the files, and cut-and-paste their contents into the scoreboard web page, and you pwn this game.
All in all, it was a very fun, but exhausting, weekend. I learned a lot… some of it security-related, and some… well… Thanks to the organizers for another fun weekend. I am glad that they only hold this thing once per year.
—
[1] I am also willing to accept an alternative explanation – that I am too dumb to understand what Justin was talking about.
Encrypting your entire hard disk (almost)
0I have a small netbook that I use when I travel, one of the original Asus EeePC’s, the 900. It has a 9″ screen and a 16GB flash drive. It runs Linux, and it’s just about right for accessing email, some light surfing, and doing small tasks like writing blog posts and messing with my checkbook. And since it runs Linux, I can do a lot of nice network stuff with it, like SSH tunneling, VPN’s, and I can even make it act like a wireless access point.
However, the idea of leaving my little PC in a hotel room while I am out having fun leaves me a little uneasy. I am not concerned with the hardware… it’s not worth much. But I am concerned about my files, and the temporary files like browser cookies and cache. I’d hate for someone to walk away with my EeePC and also gain access to
countless other things with it.
So this week, I decided to encrypt the main flash drive. Before, the entire flash device was allocated as one device:
partition 1 – 16GB – the whole enhilada
Here’s how I made my conversion.
(0) What you will need:
- a 1GB or larger USB stick (to boot off of)
- an SD card or USB drive big enough to back up your root partition
(1) Boot the system using a “live USB stick” (you can create one in Ubuntu by going to “System / Administration / Startup Disk Creator”. Open up a terminal and do “sudo -i” to become root.
ubuntu@ubuntu:~$ sudo -i root@ubuntu:~$ cd / root@ubuntu:/$
(2) Install some tools that you’ll need… they will be installed in the Live USB session in RAM, not on your computer. We’ll install them on your computer later.
root@ubuntu:/$ apt-get install cryptsetup
(3) Insert an SD card and format it. I formatted the entire card. Sometimes, you might want to make partitions on it and format one partition.
root@ubuntu:/$ mkfs.ext4 /dev/sdb root@ubuntu:/$ mkdir /mnt/sd root@ubuntu:/$ mount /dev/sdb /mnt/sd root@ubuntu:/$
(4) Back up the main disk onto the SD card. The “numeric-owner” option causes the actual owner and group numbers to be stored in the tar file, rather than trying to match the owner/group names to the names from /etc/passwd and /etc/group (remember, we booted from a live USB stick).
root@ubuntu:/$ tar --one-file-system --numeric-owner -zcf /mnt/sd/all.tar.gz . root@ubuntu:/$
(5) Re-partition the main disk. I chose 128MB for /boot. The rest of the disk will be encrypted. The new layout looks like this:
partition 1 – 128MB – /boot, must remain unencrypted
partition 2 – 15.8GB – everything else, encrypted
root@ubuntu:/$ fdisk -l Disk /dev/sda: 16.1 GB, 16139354112 bytes 255 heads, 63 sectors/track, 1962 cylinders Units = cylinders of 16065 * 512 = 8225280 bytes Sector size (logical/physical): 512 bytes / 512 bytes I/O size (minimum/optimal): 512 bytes / 512 bytes Disk identifier: 0x0002d507 Device Boot Start End Blocks Id System /dev/sda1 * 1 17 136521 83 Linux /dev/sda2 18 1962 15623212+ 83 Linux root@ubuntu:/$
(6) Make new filesystems on the newly-partitioned disk.
root@ubuntu:/$ mkfs.ext4 /dev/sda1 root@ubuntu:/$ mkfs.ext4 /dev/sda2 root@ubuntu:/$
(7) Restore /boot to sda1. It will be restored into a “boot” subdirectory, because that’s the way it was on the original disk. But since this is a stand-alone /boot partition, we need to move the files to that filesystem’s root.
root@ubuntu:/$ mkdir /mnt/sda1 root@ubuntu:/$ mount /dev/sda1 /mnt/sda1 root@ubuntu:/$ cd /mnt/sda1 root@ubuntu:/mnt/sda1$ tar --numeric-owner -zxf /mnt/sd/all.tar.gz ./boot root@ubuntu:/mnt/sda1$ mv boot/* . root@ubuntu:/mnt/sda1$ rmdir boot root@ubuntu:/mnt/sda1$ cd / root@ubuntu:/$ umount /mnt/sda1 root@ubuntu:/$
(8) Make an encrypted filesystem on sda2. We will need a label, so I will call it “cryptoroot”. You can choose anything here.
root@ubuntu:/$ cryptsetup luksFormat /dev/sda2 WARNING! ======== This will overwrite data on /dev/sda2 irrevocably. Are you sure? (Type uppercase yes): YES Enter LUKS passphrase: ******** Verify passphrase: ******** root@ubuntu:/$ cryptsetup luksOpen /dev/sda2 cryptoroot root@ubuntu:/$ mkfs.ext4 /dev/mapper/cryptoroot root@ubuntu:/$
(9) Restore the rest of the saved files to the encrypted filesystem that lives on sda2. We can remove the extra files in /boot, since that will become the mount point for sda1. We need to leave the empty /boot directory in place, though.
root@ubuntu:/$ mkdir /mnt/sda2 root@ubuntu:/$ mount /dev/mapper/cryptoroot /mnt/sda2 root@ubuntu:/$ cd /mnt/sda2 root@ubuntu:/mnt/sda2$ tar --numeric-owner -zxf /mnt/sd/all.tar.gz root@ubuntu:/mnt/sda2$ rm -rf boot/* root@ubuntu:/mnt/sda2$ cd / root@ubuntu:/$
(10) Determine the UUID’s of the sda2 device and the encrypted filesystem that sits on top of sda2.
root@ubuntu:/$ blkid /dev/sda1: UUID="285c9798-1067-4f7f-bab0-4743b68d9f04" TYPE="ext4" /dev/sda2: UUID="ddd60502-87f0-43c5-aa28-c911c35f9278" TYPE="crypto_LUKS" << [UUID-LUKS] /dev/mapper/root: UUID="a613df67-3179-441c-8ce5-a286c16aa053" TYPE="ext4" << [UUID-ROOT] /dev/sdb: UUID="41745452-3f89-44f9-b547-aca5a5306162" TYPE="ext3" root@ubuntu:/$
Notice that you’ll also see sda1 (/boot) and sdb (the SD card) as well as some others, like USB stick. Below, I will refer to the actual UUID’s that we read here as [UUID-LUKS] and [UUID-ROOT].
(11) Do a “chroot” inside the target system. A chroot basically uses the kernel from the Live USB stick, but the filesystem from the main disk. Notice that when you do this, the prompt changes to what you usually see when you boot that system.
root@ubuntu:/$ mount /dev/sda1 /mnt/sda2/boot root@ubuntu:/$ mount --bind /proc /mnt/sda2/proc root@ubuntu:/$ mount --bind /dev /mnt/sda2/dev root@ubuntu:/$ mount --bind /dev/pts /mnt/sda2/dev/pts root@ubuntu:/$ mount --bind /sys /mnt/sda2/sys root@ubuntu:/$ chroot /mnt/sda2 root@enigma:/$
(12) Install cryptsetup on the target.
root@enigma:/$ apt-get install cryptsetup root@enigma:/$
(13) Change some of the config files on the encrypted drive’s /etc so it will know where to find the new root filesystem.
root@enigma:/$ cat /etc/crypttab cryptoroot UUID=[UUID-LUKS] none luks root@enigma:/$ cat /etc/fstab proc /proc proc nodev,noexec,nosuid 0 0 # / was on /dev/sda1 during installation # UUID=[OLD-UUID-OF-SDA1] / ext4 errors=remount-ro 0 1 UUID=[UUID-ROOT] / ext4 errors=remount-ro 0 1 /dev/sda1 /boot ext4 defaults 0 0 # RAM disks tmpfs /tmp tmpfs defaults 0 0 tmpfs /var/tmp tmpfs defaults 0 0 tmpfs /var/log tmpfs defaults 0 0 tmpfs /dev/shm tmpfs defaults 0 0 root@enigma:/$
(14) Rebuild the GRUB bootloader, since the files have moved from sda1:/boot to sda1:/ .
root@enigma:/$ update-grub root@enigma:/$ grub-install /dev/sda root@enigma:/$
(15) Update the initial RAM disk so it will know to prompt for the LUKS passphrase so it can mount the new encrypted root filesystem.
root@enigma:/$ update-initramfs -u -v root@enigma:/$
(16) Reboot.
root@enigma:/$ exit root@ubuntu:/$ umount /mnt/sda2/sys root@ubuntu:/$ umount /mnt/sda2/dev/pts root@ubuntu:/$ umount /mnt/sda2/dev root@ubuntu:/$ umount /mnt/sda2/proc root@ubuntu:/$ umount /mnt/sda2/boot root@ubuntu:/$ umount /mnt/sda2 root@ubuntu:/$ reboot
When it has shut down the Live USB system, you can remove the USB stick and let it boot the system normally. If all went well, you will be prompted for the LUKS passphrase a few seconds into the bootup process.
Vacation in Hawaii
0In April, our family went on a vacation in Hawaii. My parents went with us, and we spent a week on Oahu, the “main island”. We stayed in Waikiki Beach, which is just southwest of Honolulu.
Wednesday 2011-04-13
Wednesday was a long travel day. We woke up at 3am to get ready for our early flight out, hopping across the country, finally to arrive in Honolulu at 6pm (plus six hours time zone difference). By the time we got to the hotel and had supper, it had been a 24-hour travel day.
Thursday 2011-04-14
Thursday started at 2am, when Foong’s ipod alarm clock (still on Eastern time) went off. She woke us up, claiming that it was 8am and that we needed to get ready for our “orientation breakfast”. After our long day before and a half-night’s rest, no one wanted to get up. It would be several hours before some of us were alert enough to figure out what had happened.
At the real 8am, we were ready to get up, and so we went to an “orientation breakfast”. That’s a free welcome breakfast, sponsored by the hotel and many local businesses, where they tell you all about Hawaii and give suggestions on what to do. We got suckered into taking a shuttle bus “to our hotel” by way of a museum and jewelry store, where they show you how coral is collected and polished into jewelry. I spent most of my effort convincing Sydney that she would not get to open an oyster and discover (purchase) a pearl. This game would last all week.
When we finally caught the shuttle back to our hotel, we decided tp declare our independence from our breakfast-feeding captors. So we took our van and drove through Waikiki beach and to Diamond Head crater. The trail to the top was closed for repairs, but we got to watch a helicopter taking supplies up to the top of the trail. We found a geocache, and then headed out to explore some more.
One place we explored was Safeway. We wanted to pick up breakfast stuff for the hotel, and some snacks and drinks for when we’re out. They had a full lunch buffet, so we ate there and we watched the locals shop… an adventure in itself.
We spent the afternoon at our hotel, on the beach and at the pool.
Friday 2011-04-15
On Friday, we visited Pearl Harbor. We saw the submarine USS Bowfin, the Arizona memorial, and the USS Missouri battleship. It wasn’t a day that will live in infamy, but it was a sobering, educational trip.
Saturday 2011-04-16
We spent Saturday at the Polynesian Cultural Centure, which is on the Northeast side of Oahu. This is a Polynesian-themed park that is run by the nearby Brigham Young University – Hawaii. Like most of the park’s employees, our tour guides, Liam from New Zealand and Kotona from Japan, were BYU-H students. We visited villages from Hawaii, Samoa, Aotearoa (New Zealand), Fiji, Tahiti and Tonga. Each village had activities which showcase some aspect of Polynesian life. We had dinner at a Luau, and later saw their eveng show, “H?: Breath of Life”.
The trip to the Polynesian Cultural Centure was definitely a highlight of our visit to Hawaii.
Sunday 2011-04-17
On Sunday, we drove to the North Shore to visit the Dole Plantation. We took a ride on their mini-train, where they showed all of the different types of tropical crops that are grown in the area. The most surprising part of our visit was learning that pineapples grow as blooms on the top of small bushes (I had always imagined them hanging from trees, like bananas or coconuts). While we were on the train, it started raining. Unfortunately, this was a long tropical mountain rain that did not let up, and so the rest of our visit was spent inside the gift shop.
We left the plantation and drove on to the North Shore. Although the drive was only 8 miles, the landscape and weather changed dramatically along the way. It was sunny and warm in Haleiwa, and so we got out and walked on the beach. We also spent some time just up the road at Waimea Bay Beach Park. The sand on the North Shore is a beautiful mix of shell fragments and volcanic pieces (especially compared to the sand at our hotel in Waikiki, which is trucked in from somewhere else, because of years of erosion).
Monday 2011-04-18
On Monday, we went snorkeling in Hanauma Bay, a bay that formed in an old volcano crater. The floor of the bay is covered in coral, and you can easily see tropical fish and other wildlife. This was an excellent place for a family to try snorkeling for the first time, because there are few waves and currents, the water is not very deep, and it’s easy to go from the snorkeling area back to the beach. We saw all sorts of fish, and we even saw an octopus — and on the shore, there were chickens!
In the afternoon, we walked over to the Hilton to see their “Hawaiian Village”, which I thought was supposed to be some sort of display of native Hawaiian culture. Instead, what we found was a collection of fancy shops that surrounds the Hilton’s pool pavilion. It was nice, but not what I had expected. The real shocker was seeing their display of African Black-Footed Penguins… in Hawaii??
We spent the rest of the day hanging around the pool and the outdoor restaurant at our hotel.
Tuesday 2011-04-19
We did some rough calculations, and we decided that it would be a good idea to do at least one load of laundry before we had to start “recycling”. So we consulted the internet and made an elaborate plan to have our breakfast in Waikiki, just down the street from a laundromat. This would also give us a chance to explore downtown Waikiki. So we got the van, found a place to park, started a load, had breakfast, found a geocache, moved the clothes to the dryer, explored Waikiki some, and picked up our clothes. We were so proud of how clever we were. (Later, we discovered that our own hotel had a coin laundry in the basement, but it never occurred to us to check that close to home base!!!)
From there, we headed into downtown Honolulu to explore the ‘Iolani Palace, which was the official residence of King Kal?kaua and Queen Lili’uokalani. Inside the palace, we learned about how the many tribes of Hawaii were united by King Kamehameha, and later how the queen complied under protest to the forceful annexation by the United States.
From there, we visited the Aloha Tower, which overlooks Honolulu Harbor, and is surrounded by shops.
I had made up my mind that it was time to experience an authentic Hawaiian meal, so we went to a place called “Kaka’ako Kitchen”. It’s not much in terms of atmosphere, but it’s supposed to be good food. I had Loco Moco and Nalo Greens… which I discovered was really just country chopped steak with gravy and a green salad. So much for culture.
Wednesday 2011-04-20
We woke up Wednesday morning and headed back over to the Hilton’s “lagoon”, where the girls rented a paddleboard, which is like a large surfboard that they stand on and paddle with a long oar.
We had already seen the beaches, volcanoes, the city, and Pearl Harbor, but we still had not seen the tropical rainforest. So after lunch, we decided to take a hike on the Manoa Falls trail. According to the guide book that we read, this was supposed to be an “easy” trail, perfect for families. In reality, although it was less than a mile long (one way), it was steep and muddy, and slippery in many parts. The scenery along the path was amazing, with a thick forest at the base, then twisted viney trees, large clusters of bamboo, and finally an opening at the foot of a 100-foot waterfall.
After our hike, we had a little bit of afternoon daylight left, so we drove up to punchbowl crater, which is a large dormant volcano surrounded by a residential neighborhood in Honolulu. Inside the crater is the National Memorial Cemetery of the Pacific.
Thursday 2011-04-21
Our flight back home was at 9pm, so we had most of Thursday free to explore. We packed up and checked out of the hotel, and then Audrey and I bought one last souvenir, a ukulele.
Our final tourist attraction was Bishop Museum, which has exhibits on everything from early Polynesian culture to lava and volcanoes.
Thursday 2011-04-14
Thursday started at 2am, when Foong’s ipod alarm clock (still on Eastern time) went off. She woke us up, claiming that it was 8am and that we needed to get ready for our “orientation breakfast”. After our long day before and a half-night’s rest, no one wanted to get up. It would be several hours before some of us were alert enough to figure out what had happened.
At the real 8am, we were ready to get up, and so we went to an “orientation breakfast”. That’s a free welcome breakfast, sponsored by the hotel and many local businesses, where they tell you all about Hawaii and give suggestions on what to do. We got suckered into taking a shuttle bus “to our hotel” by way of a museum and jewelry store, where they show you how coral is collected and polished into jewelry. I spent most of my effort convincing Sydney that she would not get to open an oyster and discover (purchase) a pearl. This game would last all week.
When we finally caught the shuttle back to our hotel, we decided tp declare our independence from our breakfast-feeding captors. So we took our van and drove through Waikiki beach and to Diamond Head crater. The trail to the top was closed for repairs, but we got to watch a helicopter taking supplies up to the top of the trail. We found a geocache, and then headed out to explore some more.
One place we explored was Safeway. We wanted to pick up breakfast stuff for the hotel, and some snacks and drinks for when we’re out. They had a full lunch buffet, so we ate there and we watched the locals shop… an adventure in itself.
We spent the afternoon at our hotel, on the beach and at the pool.
Friday 2011-04-15
On Friday, we visited Pearl Harbor. We saw the submarine USS Bowfin, the Arizona memorial, and the USS Missouri battleship. It wasn’t a day that will live in infamy, but it was a sobering, educational trip.
Saturday 2011-04-16
We spent Saturday at the Polynesian Cultural Centure, which is on the Northeast side of Oahu. This is a Polynesian-themed park that is run by the nearby Brigham Young University – Hawaii. Like most of the park’s employees, our tour guides, Liam from New Zealand and Kotona from Japan, were BYU-H students. We visited villages from Hawaii, Samoa, Aotearoa (New Zealand), Fiji, Tahiti and Tonga. Each village had activities which showcase some aspect of Polynesian life. We had dinner at a Luau, and later saw their eveng show, “H?: Breath of Life”.
The trip to the Polynesian Cultural Centure was definitely a highlight of our visit to Hawaii.
Sunday 2011-04-17
On Sunday, we drove to the North Shore to visit the Dole Plantation. We took a ride on their mini-train, where they showed all of the different types of tropical crops that are grown in the area. The most surprising part of our visit was learning that pineapples grow as blooms on the top of small bushes (I had always imagined them hanging from trees, like bananas or coconuts). While we were on the train, it started raining. Unfortunately, this was a long tropical mountain rain that did not let up, and so the rest of our visit was spent inside the gift shop.
We left the plantation and drove on to the North Shore. Although the drive was only 8 miles, the landscape and weather changed dramatically along the way. It was sunny and warm in Haleiwa, and so we got out and walked on the beach. We also spent some time just up the road at Waimea Bay Beach Park. The sand on the North Shore is a beautiful mix of shell fragments and volcanic pieces (especially compared to the sand at our hotel in Waikiki, which is trucked in from somewhere else, because of years of erosion).
Monday 2011-04-18
On Monday, we went snorkeling in Hanauma Bay, a bay that formed in an old volcano crater. The floor of the bay is covered in coral, and you can easily see tropical fish and other wildlife. This was an excellent place for a family to try snorkeling for the first time, because there are few waves and currents, the water is not very deep, and it’s easy to go from the snorkeling area back to the beach. We saw all sorts of fish, and we even saw an octopus — and on the shore, there were chickens!
In the afternoon, we walked over to the Hilton to see their “Hawaiian Village”, which I thought was supposed to be some sort of display of native Hawaiian culture. Instead, what we found was a collection of fancy shops that surrounds the Hilton’s pool pavilion. It was nice, but not what I had expected. The real shocker was seeing their display of African Black-Footed Penguins… in Hawaii??
We spent the rest of the day hanging around the pool and the outdoor restaurant at our hotel.
Tuesday 2011-04-19
We did some rough calculations, and we decided that it would be a good idea to do at least one load of laundry before we had to start “recycling”. So we consulted the internet and made an elaborate plan to have our breakfast in Waikiki, just down the street from a laundromat. This would also give us a chance to explore downtown Waikiki. So we got the van, found a place to park, started a load, had breakfast, found a geocache, moved the clothes to the dryer, explored Waikiki some, and picked up our clothes. We were so proud of how clever we were. (Later, we discovered that our own hotel had a coin laundy in the basement, but it never occured to us to check that close to home base!!!)
From there, we headed into downtown Honolulu to explore the ‘Iolani Palace, which was the official residence of King Kal?kaua and Queen Lili’uokalani. Inside the palace, we learned about how the many tribes of Hawaii were united by King Kamehameha, and later how the queen complied under protest to the forceful annexation by the United States.
From there, we visited the Aloha Tower, which overlooks Honolulu Harbor, and is surrounded by shops.
I had made up my mind that it was time to experience an authentic Hawaiian meal, so we went to a place called “Kaka’ako Kitchen”. It’s not much in terms of atmosphere, but it’s supposed to be good food. I had Loco Moco and Nalo Greens… which I discovered was really just country chopped steak with gravy and a green salad. So much for culture.
Wednesday 2011-04-20
We woke up Wednesday morning and headed back over to the Hilton’s “lagoon”, where the girls rented a paddleboard, which is like a large surfboard that they stand on and paddle with a long oar.
We had already seen the beaches, volcanos, the city, and Pearl Harbor, but we still had not seen the tropical rainforest. So after lunch, we decided to take a hike on the Manoa Falls trail. According to the guide book that we read, this was supposed to be an “easy” trail, perfect for families. In reality, although it was less than a mile long (one way), it was steep and muddy, and slippery in many parts. The scenery along the path was amazing, with a thick forest at the base, then twisted viney trees, large clusters of bamboo, and finally an opening at the foot of a 100-foot waterfall.
After our hike, we had a little bit of afternoon daylight left, so we drove up to punchbowl crater, which is a large dormant volcano surrounded by a residential neighborhood in Honolulu. Inside the crater is the National Memorial Cemetery of the Pacific.
Thursday 2011-04-21
Our flight back home was at 9pm, so we had most of Thursday free to explore. We packed up and checked out of the hotel, and then Audrey and I bought one last souvenir, a ukulele.
Our final tourist attraction was Bishop Museum, which has exhibits on everything from early Polynesian culture to lava and volcanos.
A Tech Trifecta
2Dropbox + KeePass + VeraCrypt
I would like to introduce three software packages that are profoundly useful in their own rights, but then go a step further and show how these three tools can be used together to revolutionize how you keep track of your secrets & finances in the digital age.
The first tool is Dropbox, a cloud service where you can store a folder of your own personal files. They offer a free service where you can keep 2GB of files, and you can pay for more storage.
You can access the files from anywhere using a web interface. Or better, you can install the Dropbox program, and it will automatically keep a local copy of all of your stuff up to date in a folder on your computer (Windows, Mac or Linux). If you’re offline for a bit, no problem, because you still have your local copy of the files.
The real magic happens when you connect multiple computers to the same Dropbox account — say, your home PC and your office PC. Dropbox keeps the files in sync for you.
There is even a Dropbox app for your iPhone, so you can access your files on the go.
If I asked you how many passwords you have, you might think that you have a dozen or so. One day, I decided to make a list of every password I had (including multiple accounts where I happened to use the same password). I was shocked to find that I had more than 100.
PRO TIP – Most people use the same five passwords over and over… they don’t bother remembering which ones they used for a particular web site… they just try all five of their “not so important” passwords. That means that if I want to steal something from you, I can just set up a service and invite you to log in. I make your next login attempt fail, so you’ll get confused and enter all five of your “not so important” passwords, and possibly your “good” ones, too. Then I can go to eBay and PayPal and Amazon with your username and all of your passwords, and I have a pretty good chance of logging into your account.
For this reason, you should use a different password at EVERY web site.
KeePass is an open source program that stores your passwords. The program stores all of that information in a single data file that you lock using a single “master password”. This should be the only password you ever remember. The rest of them should be long strings of gibberish characters.
Keepass has a nice “generate” feature which will come up with really good passwords like “an@aiph5Ph”.
KeePass is available for Windows, Mac and Linux (KeePassX), and there are a couple of iPhone variants (I recommend “MyKeePass”).
Keepass stores four main fields: the browser URL address, user name, password, and notes. That means that I can store an entry like this for my bank:
URL = https://www.FirstFederalLovesYou.com/personal/login
name = alan_porter
password = uG7pi~ji9a
notes = security question, pet’s name = teabag
These days, it’s really easy to get confused about the main web address that you’re supposed to use to log in to your bank. They make things confusing by using fancy URL’s like “FirstFederalLovesYou.com” instead of “FirstFederal.com”. If you have not had your coffee one morning and you type “FirstFederalLovesMe.com” by mistake (“Me” instead of “You”), you’ll find yourself logging into a phishing site, which is trying to steal your password.
With keepass, there is no room for this sort of error. You double click on the URL and a browser opens on that site. You double click on the user name and it copies the user name to the clipboard. Paste it in the browser. Similarly, double click on the password and paste it in the browser. If your bank uses “security questions”, you can store your answers in the notes section.
PRO TIP – Don’t use truthful answers for “security” questions… treat these as extended passwords, just like you’d see in the old spy movies (he says “the sky looks like rain”, and you answer “that helps the bananas grow”). The answers do not even need to make sense… they just need to be remembered… in your head (bad) or in your KeePass file (good).
And no, I have never had a pet named “teabag”.
The last tool I would like to talk about is VeraCrypt*, a free package that allows you to create an encrypted volume on a file or a disk.
NOTE: the original version of this blog post recommended TrueCrypt, which has been discontinued — VeraCrypt is a drop-in replacement with several improvements, most notably it is open source and it has undergone very close scrutiny and security audits.
You can create a VeraCrypt file with a name like “mysecrets.vc” that you store on your desktop. You give it a size and a password. Then when you open that file, you’ll have to enter the password, and then it will appear as a Windows drive letter. On a Mac or Linux, it will show up as folder in /Volumes or in /media. When you close it, the drive letter is gone, and your secrets are stored, encrypted, in the “mysecrets.vc” file.
You can store this “mysecrets.vc” file anywhere you want… on your desktop, on a USB flash drive, or even on your Dropbox account.
You might also want to use VeraCrypt to encrypt an entire device, like a USB flash drive or SD card — nice.
THE TRIFECTA
Using these three tools together, suddenly we have a very secure way to do our online banking.
Regardless of what computer you’re using — Mac, Windows, Linux, desktop, laptop, at home, at work, whatever — you now have access to your passwords, and all of the other files that you need: Quicken or GnuCash, the PDF files of your bills, personal files, etc.
EXAMPLE 1 – PAYING BILLS FROM A WINDOWS PC
A typical online bill-paying session might look like this:
- Look in your Dropbox for your KeePass password file, say D:\mypasswords.kdb. Open it with KeePass.
- Look in your Dropbox for your VeraCrypt volume, say D:\mybills.vc. Open it with VeraCrypt. It will be mounted as drive V.
- Use your normal accounting package (Quicken or Gnucash) to open your checkbook, say V:\checkbook.qdf or V:\checkbook.gc.
- Find your bank password in KeePass. Click on the safe URL, copy the username and password from KeePass to the browser.
- When you need to save a statement or a bill, save into the VeraCrypt volume on the V drive, like in V:\statements.
EXAMPLE 2 – LOOKING UP A PASSWORD FROM THE IPHONE
Say you’re out and about, and you want to use your iphone to log into a web site that you don’t know the password for (of course you don’t… because you use GOOD and UNIQUE passwords like “taeYi#c6We”, right?).
- First, you use the iPhone Dropbox app to locate your KeePass file. Click on the filename, and the app will say “I don’t know what kind of file this is”. But it will show you a little “chain link” icon in the bottom. Click this icon to get a web URL for that one file. The URL will be copied to your clipboard.
- Next, run MyKeePass and click “+” to add a new KeePass file. Select “download from WWW” and paste the URL that you just got from Dropbox.
Now, you can open your KeePass file from anywhere! You’ll have to enter the file’s master password that you set up earlier. After that, you’ll be able to browse the information in the KeePass file.
Note that you can only READ the file using the “download from WWW” method. If you need to save a new password or some other information, you’ll need to write it down on a piece of paper until you are back at your PC (no biggie — that’s pretty rare).
A NOTE ABOUT SECURITY
Some readers might note that we just shared our KeePass password file with the entire world, when we told Dropbox to give us a URL. Someone else could use that same (random-ish) URL to download our KeePass file. Since this file is encrypted using the master password, it will look like gibberish to anyone but you. For this reason, we should make sure that we use a VERY STRONG password for the KeePass file… not your dog’s name (remember, mine is “teabag”).
Using SSH to tunnel web traffic
1Every once in a while, I learn something new and magical that SSH can do. For a while now, I have been using its “dynamic port forwarding” capability, and I wanted to share that here.
Dynamic port forwarding is a way to create a SOCKS proxy that listens on your local machine, and forwards all traffic through the SSH tunnel to the remote side, where it will be passed along to the remote network.
What this means is that you can tell your web browser to send some – or all – of your web requests through the tunnel, and the SSH daemon on the other side will send those requests out to the internet for you, and then it will send the responses back through the tunnel to your browser.
There are several practical uses for SSH tunneling. Here are a few real-world examples of where I have used tunnels:
- You may be behind a firewall that blocks web sites that you want to visit. I was at a company that had a web proxy that blocked some “hacking” web sites, when I really needed to look up some information on computer vulnerabilities, to make sure that their systems were properly patched. Using the SSH tunnel bypassed that company’s web proxy.
- You may not trust a hotel’s internet service. In fact, you SHOULD NOT trust a hotel’s internet service. They keep records of sites that you visit, ostensibly to keep a customer profile of your interests. Some also do deep packet inspection to observe words in the web pages and emails that you read. Intrusive marketing!
- You may want to work from home, and access work lab resources from home. If you can SSH into one machine at work, then you can access the web resources inside that network.
- Working on a cluster of machines, where only one of them is directly accessible from your desk. It stinks to have to do your work in a noisy lab. Why not shell into the gateway machine and tunnel your web traffic through that SSH connection?
- You may want to access a web interface to something at home, like a printer… or an oven. You should open the SSH service to your router, and then you can SSH in and easily access web interfaces to everything in your home.
- You may want a web interface on some service on an internet-facing machine, but you don’t want to expose it to everyone. Maybe you want phpMyAdmin on a server, but you don’t want everyone to see it. So run the web service on the local (127.0.0.1) network only, and use an SSH tunnel to get to it from wherever you are.
- Your ISP throttles web traffic from a particular site. In my case, it was an overseas movie streaming site, and my ISP would limit my traffic to 300kbps for 30 seconds, followed by nothing for 30 seconds (they do this to discourage you from watching movies over the internet). Sending the traffic through an SSH tunnel means the ISP only sees an encrypted stream of something on port 22 — they have no idea that the content is actually a movie streamed from China on port 80.
- You may live in India, but want to watch a show on Hulu (which only serves the US market). By tunneling through a US-based server, it will appear to Hulu that you’re in the US.
- You may be visiting China, and you want to bypass the Great Firewall of China. Believe it or not, my humble domain was not accessible directly from Shanghai.
- You may get a “better” route by going through a proxy. This is speculation on my part… but I did this once when I was in a free-for-all online ticket purchase. I wondered if I might get a faster route from my remote data center than I would get directly from my ISP.
So, how do you create a tunnel? It’s super easy.
Create an SSH session with a tunnel.
On Linux or a Mac, open a shell and type “ssh -D 10000 username@remotehost.com“.
On Windows*, you can run Putty (an SSH client). In the “connection / SSH / tunnels” menu, click on “dynamic”, then enter source port = 10000, then click “add”. You’ll see a “D10000” in the box that lists your forwarded ports. (* Putty is also available for Linux.)
That’s it… you’re done.
Tell the browser to use the tunnel.
The easiest way to get started with SOCKS proxies is to set it in the “preferences / advanced / network / connection settings” menu in Firefox (or the “preferences / under the hood / change proxy settings” menu in Google Chrome). In both cases, you want to set “manual proxy configuration” and SOCKS host = “localhost” and SOCKS port = 10000. If there is a selection for SOCKS v5, then check it.
Now, all web requests will go to a proxy that is running on your local machine on port 10000. If you do a “netstat -plnt | grep 10000”, you’ll see that your SSH or Putty session is listening on port 10000. SSH then forwards the web request to the remote machine, where SSHD will send it on out to the internet. Web responses will come back along that same path.
Anyone on your local network will only be able to see one connection coming from your machine: an encrypted SSH session to the remote. They will not see the web requests or responses. This makes it a great tool for using on public networks, like coffee shops or libraries.
Test it
Point your browser to a site that tells you your IP address, such as whatismyip.com. It should report the IP address of the remote server that you are connecting through, and not your local IP address.
Advanced – quickly selecting proxies using FoxyProxy or Proxy Switchy!
It can be a hassle to go into the preferences menu to turn the proxy on and off. So there are browser plug-ins that allow you to quickly switch between a direct connection and using a SOCKS proxy.
For Firefox, there is the excellent “FoxyProxy“. For Chrome, you’ll want “Proxy Switchy!“. Both plug-in’s allow you to select a proxy using a button on the main browser window.
But there’s more… they also allow you build a list of rules to automatically switch based on the URL that you are browsing. For example, at work, I set up a rule to route all web requests for the lab network through my SSH session that goes to the lab gateway machine.
It works like this. First, I set up a tunnel to the lab gateway machine:
- ssh -D 10001 alan@192.168.100.1 (lab gateway)
Then I set up the following FoxyProxy rules:
- 192.168.100.* – SOCKS localhost:10001 (SSH to lab)
- anything else – direct
Now, I can get to the lab machines using the lab proxy, and any other site that I access uses the normal corporate network.
Closing thoughts
If you like Putty or FoxyProxy or Proxy Switchy!, please consider donating to the projects to support and encourage the developers.