alan
Alan Porter is a mobile application developer, a nerd, a father, and a friend. He is really into gadgets and open source software, and he has spent most of his career making these two things work -- sometimes together. These days, you'll usually find him tinkering with his iPhone. He lives in NC with his lovely Malaysian wife and his two daughters.
Home page: http://alanporter.com
Posts by alan
Rush Concert
1I saw my first rock concert in November 1986… Journey, Greensboro. But that is another story.
A year later, my second concert was Rush in Charlotte. My friends and I drove down from NC State to see their “Hold Your Fire” tour. An excellent show, and one that left a memorable impression.
Shortly after the show, the band announced more tour dates, including one at Reynolds Coliseum in Raleigh, just a few hundred feet from my dorm room! So my friends and I got tickets for that one, too. On the day of the show, I won 2nd row tickets from our campus radio station, WKNC. We were so close, I felt like I could high-five Geddy Lee.
Fast forward 25 years, and now I have a family. I don’t listen to classic rock that much, but I do try to raise my kids right, teaching them to pick out the important bands like Rush or Van Halen just from their style. My older daughter has a good ear for that sort of thing, but my younger one simply guesses the same names for every song: Beatles, Prince, Van Halen. Prince?? Really?
Last night, Rush came to PNC Arena in Raleigh as part of their Clockwork Angels tour, and I brought the family to see these legends of rock-n-roll. We were not quite “high-five” close, but we had great seats — 18th row beside the stage (on Geddy Lee’s side, of course).
For a bunch of 60-year-olds, the trio put on a great show. Geddy Lee couldn’t hit the high notes that he could in the 80’s, but that did not slow them down at all.
The stage was decorated in a steampunk theme, with lots of mechanical gear, and even a popcorn machine (at one point, a stagehand snuck on stage and grabbed some popcorn).
The show was divided into three sets: two halves and a so-called “encore”.
The first set was mostly from Moving Pictures, Signals, Power Windows, and Hold Your Fire (1981-1987). This was the Rush that I came to see.
The second set dove into a lot of new stuff from the last 10 years that I am not really familiar with. It was enjoyable, but not epic. They spiced up this part of the show, first with a hard-rockin’ string ensemble backup, and then later with some surprise pyrotechnics. Towards the end of this set, Sydney actually drifted off to sleep… at a rock concert.
They finished up with an encore set of classics from Moving Pictures and 2112.
Play List
Set One
|
Set Two
|
Encore:
|
News & Observer photos
 |
 |
 |
 |
 |
 |
Moving a domain to a new registrar
1This week, I moved the “trilug.org” domain from GoDaddy to NameCheap. Our renewal time was coming up. And at the same time, we were discussing a new policy of inclusiveness and a code of proper conduct for the group. I had long felt that GoDaddy’s branding was “tacky”, and did not really align with the direction that TriLUG was heading. Really… GoDaddy Girls? It wouldn’t be appropriate to hold our meetings at Hooters, and we feel the same way about the GoDaddy Girls.
If you’ve never moved a domain from one registrar to another, it can be confusing. There are several interlocking steps that have to be done in a certain order. If you have a roadmap, it can take an hour or so. If not, you can waste a day or more waiting for all of the steps to complete.
This is the recipe that I have followed for several transfers.
From GoDaddy to NameCheap
- GoDaddy:unlock domain
- GoDaddy: send EPP (authorization code) via email
- NameCheap: initiate transfer
- NameCheap: fill in EPP codes
- NameCheap: use coupon code “SWITCH2NC”, save $1/domain
- NameCheap: submit transfer order, pay
- wait for email from NameCheap
- receive email from transfer-domain.com (for NameCheap)
- click on link, agree to the transfer
- wait for email from GoDaddy
- receive email from GaDaddy
- GoDaddy: pending transfers, accept or decline
- you’re done – wait for email confirmations
- email from GoDaddy, domain is transferred
- whois reports new registrar
- email from NameCheap, welcome
At this point, it’s a good idea to double-check that your DNS settings transferred correctly. Mine always have.
I hope that your transfer goes as smoothly as ours did.
iPhone photo gallery
0I like to keep albums of recent photos on my iPhone, so I can show them to friends and family. Not only do I keep the photos that I took on the iPhone itself, but I also keep the photos I took using other cameras. Here, I will describe the method and tools I use to keep several months worth of photos conveniently in my pocket.
At first, this seems like a very simple problem, but there are a few subtle quirks, and I have worked around them using a script and some open source tools. In the end, I will have:
- photos from multiple cameras
- selected folders, but not necessarily everything
- photos are optimized for phone size, not wasting space
- photos are oriented correctly, not sideways or upside-down
- photos from multiple cameras appear in chronological order
- process is mostly automated
The end result looks like this:
How my photos are organized
When I worked at Ericsson’s research lab in Singapore, they had done a study on how people store their digital photos and how they find a particular one in the bunch. They found that people tend to associate events with nearby dates, so they might say “Let’s see… Bill broke his leg skiing right before Janet’s wedding, so that must have been Winter of 2009”.
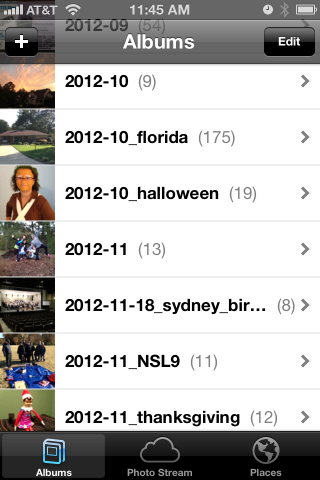
I definitely fall into that category, and so my pictures are stored in folders by date. It looks like this:
pictures - top level
+ bulk - raw unprocessed stuff, too big to browse
+ import - a working area
+ y - photo albums arranged by year/month/event
+ 2011
+ 2012
+ 2012-09
+ 2012-10
+ 2012-10_florida
+ 2012-10_halloween
+ 2012-11
+ 2012-11-12_ducks
+ 2012-11-18_sydney_birthday
+ 2012-11_NSL9
+ 2012-11_thanksgiving
+ 2013
I also want to note that some of my friends take a completely different approach… they pick a single tool and simply dump the photos into the tool. They don’t care to organize them at all and just rely on the tool. That’s certainly OK… I would guess these are the same people who don’t balance their checkbooks. If that describes you, then I suggest you stop reading here, because none of this will apply to you.
I have used the date-folder method since I got my first digital camera in 1998. It has migrated from Windows to Linux to MacOS. My data far outlasts any one tool.
So one of my assumptions is that my “pictures” directory is sacred. I do not want any tool to write anything to that directory (I am looking at you, iPhoto & iTunes).
Selecting folders (albums) to copy to the iPhone
So I set up two more directories.
- $HOME/iphone/pictures – where I say what photos to copy
- $HOME/itunes/pictures – a directory that iTunes can sync with
In the first one, $HOME/iphone/pictures, I set up a bunch of symlinks to point to the directories that I would like to copy. I do this so I can easily select some folders but leave out others.
2011-11_happy_crabby -> ../../pictures/y/2011/2011-11_happy_crabby 2012-09 -> ../../pictures/y/2012/2012-09 2012-10 -> ../../pictures/y/2012/2012-10 2012-10_florida -> ../../pictures/y/2012/2012-10_florida 2012-10_halloween -> ../../pictures/y/2012/2012-10_halloween 2012-11 -> ../../pictures/y/2012/2012-11 *** note - no ducks here *** 2012-11-18_sydney_birthday -> ../../pictures/y/2012/2012-11-18_sydney_birthday 2012-11_NSL9 -> ../../pictures/y/2012/2012-11_NSL9 2012-11_thanksgiving -> ../../pictures/y/2012/2012-11_thanksgiving
For example, let’s say I took 1000 boring photos of ducks in November. I could easily skip 2012-11-12_ducks by not creating a symlink. I can also specifically include a very old folder by leaving the symlink in this directory. I have done that here with my Happy Crabby pictures from 2011.
Copying and processing photos
I have written a script that will go through each of these directories and perform a few clean-up tasks as it copies the photos to the itunes staging area.
- It copies the photos to a temporary working directory.
We should never alter the original photos… always work with a copy.
- It rotates the image based on the EXIF orientation tag.
I’m gonna start slamming on Apple, so fanbois should cover their ears. I have found that Apple handles image rotation differently than everyone else, and it took a while to get a handle on it. I can take pictures on my iPhone and email them to someone and they’ll show up as upside-down or sideways. The images look OK on the iPhone or on a Mac, but everyone else (Linux, Windows) sees them rotated. The same thing happens if I upload them to “gallery”, an online photo gallery. Sometimes, they would show the correct dimensions but the image would still be rotated. That is, a portrait would be taller than wide, but the person’s face would be sideways and extremely elongated. The solution I found is to process them using “renrot” (see my blog post about renrot for detail).
- It renames the file using the date & time in the EXIF data.
When we get back from vacations, I find that we have photos from several different cameras, and it just seemed weird for my wife’s Nikon images (named DSCNxxxx.JPG) to appear before my iPhone images (named IMG_xxxx.JPG) and then my Panasonic images (named Pxxxxxxx.JPG) last. If I rename all of the images to (YYYY)(MM)(DD)(hh)(mm)(ss).JPG, they will appear in chronological order, regardless of which camera was used.
- It resizes the image to be no bigger than 1280 pixels high or wide.
There is no need to me to waste space on my iPhone by storing each image in their 12MP glory (actually, I typically shoot 3MP for normal vacation photos). So I resize the images using imagemagick.
- It moves the files into the iTunes directory in numerical (chronological order).
At one point, I had a problem with iTunes arranging my photos in the order that they happened to appear in the directory instead of sorted by name or anything else. If you do a “find” command on Linux or a Mac, you’ll see the files in the order that they appear in the directory file. That’s OK under the hood, because “ls” and Mac Finder and Nautilus are all smart enough to show the files in sorted order. But no, not iTunes. So I move the files from the temporary work area to the iTunes sync directory one at a time, in chronological order.
Using the script
When it’s time to sync my iPhone (less and less frequent these days, and primarily driven by when I want to update my photo albums), I simply look over the symlinks, run the script and then sync.
Running the script takes a few minutes, and syncing all of the pictures instead of just the ones that have changed takes a few minutes as well. But I am very happy with the consistent results.
I’m sure that some folks will claim that I am “doing it wrong”, that I should not have to do so many work-arounds. But the bottom line is that I encountered real-world problems from the interaction between various cameras and the quirks of iTunes, and this script smooths out all of the wrinkles. It is really no trouble to run the pre-syncing script before syncing, and it does solve the problems of images being mis-rotated, taking too much space on my phone, and appearing out of order. It also makes it trivial to choose which album folders are copied to the iPhone and which ones are not.
The script itself appears below.
The pre-syncing script
#!/bin/bash
shopt -s nocaseglob
shopt -s nullglob
src="$HOME/iphone"
dest="$HOME/itunes"
if [ ! -d "$dest" ] ; then mkdir -p "$dest" ; fi
echo "=== PHOTOS ==="
wildcard="*.[Jj][Pp][Gg] *.[Jj][Pp][Ee][Gg] *.[Pp][Nn][Gg]"
stage="/tmp/itunes.$$.stage"
mkdir -p $stage
rm -rf "$dest/pictures"
# go through each directory, and do some processing
( ls -1 $src/pictures ) | while read d ; do
# skip non-directories
[ ! -d "$src/pictures/$d/." ] && continue
echo "processing photos in [$d]"
indent=" $d >> "
# copy source photos to staging area
( cd $src/pictures/$d ; cp $wildcard $stage/ )
# rotate
echo " - rotating photos"
( cd $stage ; renrot $wildcard ) 2>/dev/null | sed -e "s/^/$indent/g"
rm $stage/*_orig 2>/dev/null
# resize
echo " - resize photos"
# iphone 4S screen is 640x960 (2xVGA)
( cd $stage ; mogrify -verbose -geometry '1280x1280>' $wildcard ) 2>/dev/null | sed -e "s/^/$indent/g"
# move to itunes area, reorder as you go
echo " - re-ordering files"
mkdir -p "$dest/pictures/$d"
ls -1 $stage | while read f ; do
# Mac bash v3 does not have ${f^^*}, so we have to use 'tr'
upper=$(echo $f | tr /a-z/ /A-Z/) # was bash internal ${f^^*}
mv -v "$stage/$f" "$dest/pictures/$(basename $d)/$upper" | sed -e "s/^/$indent/g"
done
echo ""
done
# clean up some special cases
xargsR='-r'
[ "$OSTYPE" == "darwin12" ] && xargsR='' # Mac xargs does not have -r
find $dest/pictures/ -type d -print0 | xargs -0 rmdir 2> /dev/null # empty directories
find $dest/pictures/ -name \*_orig -print0 | xargs -0 $xargsR rm -v
find $dest/pictures/ -name MEDI\*.JPG -print0 | xargs -0 $xargsR rm -v
echo ""
Halloween – traffic light costume
0Last year, at the neighborhood Halloween party, one of the kids had dressed up as a traffic light. He simply wore all black, and he had three cardboard circles attached to his front. Audrey saw that boy’s costume and got to thinking… could we build one with real lights?
This is what we came up with.
Putting it together
We had the entire year to think about it. Sometime in the summer, we actually started planning. I knew that we could do the controls, but I was not so confident about the power or how to drive several LEDs.
The controller was easy. We have been using Arduinos for several projects, and I had ordered a few “nano” boards, which are about the size of a stick of gum. We plugged one into a solderless prototyping board. We used five of the Arduino’s outputs for our five lights: red, yellow, green, “WALK” (white) and “DONT WALK” (orange). We ordered super-bright colored LEDs from DealExtreme in Hong Kong.
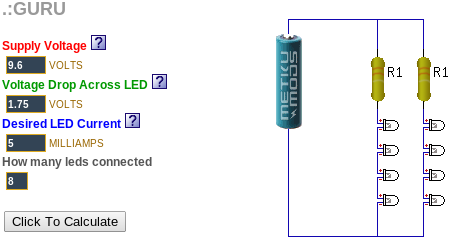
The hard part was figuring out how to power several LEDs at the same time. I discovered a web site called “ledcalc.com” that showed us how to arrange the LEDs in several serial strings wired to each other in parallel. And after taking a few measurements, we figure out what the voltage drop on each LED was and we estimated how much current to push through each LED. This suggested that we should use a higher voltage than I normally would use to just power the Arduino. We chose 8 NiMH rechargeable AA batteries for 9.6 volts.
The LED calculator suggested that for red, yellow and orange, we should plug the LEDs in strings of 4 with a small resistor at the end. We wanted 8 LEDs for each color, so that meant we’d plug two strings of 4 LEDs together in parallel.
Since the “forward voltage” (voltage drop) across the white and green LEDs was higher, we ended up using strings of 3 LEDs for those. Fortunately, they were so bright that the fewer LEDs made no difference in overall brightness.
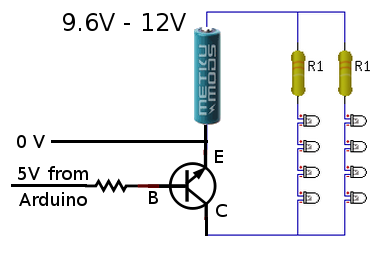
Now came the tricky part. We wanted the LEDs to run at 9.6 volts, but the Arduino runs at 5 volts. That meant we needed to use a transistor on each output to switch the higher-voltage LED strings on and off. We were able to figure out how to do this by looking at an Arduino experiment book. Below, you can see how one 5V output line from the Arduino can be used to switch 9.6V through a bank of LEDs.
During our tests, we found that after a while (a pretty long while), the white and green LEDs got very dim while the others stayed normal brightness. We decided that the battery had drained and the voltage had dropped just enough to make driving the three higher-voltage LEDs too hard. Doing a little bit of back-of-the-napkin math tells why. The white and green LEDs each have a 2.5V drop… times three LEDs and that means you have to have at least 7.5V to run them at all in series. The other color LEDs each dropped 1.75V, for a total of 7.0V. That means the white and green lights will poop out 0.5V earlier than the other colors will.
As a quick fix, we replaced the 1.2 volt NiMH rechargeable batteries with 1.5 volt alkaline batteries, making our total supply voltage a bit higher, a full 12 volts. This kept all of the LEDs bright all night. A quick estimate suggested we might get two or more DAYS worth of operation from a single set of batteries. But after watching them dim earlier, I decided to take a spare set of batteries with us while we went trick-or-treating, and I kept a close eye on the white and green LED brightness.
The big night
Halloween was a big hit. Everyone got a chuckle out of the costume, especially when Audrey turned around and they could see the WALK and DONT WALK signs.
Here is a photo of the Audrey in her stop light costume, Syndey as an Oompa Loompa and me as Harry Potter.
The Happy Crabby
0In 2009, we got a hermit crab named “Peek-a-boo”. We kept him in a plastic shoebox-sized container with creek sand in the bottom and holes drilled in the lid. He seemed to enjoy his new home, and we enjoyed his company. But some time in the winter, he died.
This turned into an annual tradition. Peek-a-boo was followed by Boo and Sprinkle in 2010, Flicker in 2011, and Blink and Barney in 2012. Some of our crabs only stayed with us a short while; others lived through the winter, but not much longer.
I wanted to know how we could take better care of them, so in 2011, we replaced the plastic box with a small glass terrarium with a glass lid. I suspected that they were getting too cold in the winter, but when I read about crabs, I found that humidity might have been a factor. I know our house gets very dry in the winter.
It was time to find measure the temperature and humidity inside the cage.
I thought about buying a simple hygrometer. We have one in our hallway . But I wanted to keep a long-running log of temperature and humidity over time.
So I decided to build an Arduino-based crab cage monitor.
The Happy Crabby
I would use an Arduino UNO to control the overall flow. I wanted to add the following peripherals:
- temperature/humidity sensor – I chose one based on the SHT11 sensor: see Adafruit or the one I got.
- real-time clock – Adafruit has a breakout board for $9.
- SD card slot – Adafruit has a breakout board for $15.
- LCD display – Adafruit has a 20×4 character LCD for $18 and an I2C-to-LCD driver board for $10.
- Relays to turn on/off a heater or light – I have not added this yet.
- Some buttons for a simple UI – I have not added this yet.
Drivers
The first thing I had to do was write some software to read the temperature and humidity from the SHT11 board. The documentation claimed that it was an I2C device, which should have made it very easy. I knew all about I2C from when I worked at Ericsson. A lot of peripherals used an I2C interface. It’s a simple two-wire protocol where you can just wiggle two output lines in a specific order to send signals to the devices. It turns out that the SHT11 is mostly I2C, but it has a strange quirk that I had to code around.
Hardware Planning
After I was receiving real temperature and humidity readings from the SHT11, I had to start allocating Arduino I/O pins to the peripherals. I made a spreadsheet to keep track of the pins. Some pins on the Arduino have special alternate uses, so I made a note of them there. Since I was working on a prototyping board, I kept changing stuff, and when I did I’d just create a new spreadsheet column. In some configurations, I did not have enough pins… specifically, if I did not use the I2C-to-LCD board, I had to allocate most of my pins to simply driving the LCD display. In other configurations, I had plenty of pins left over.
What I ended up with was this:
| PIN | FEATURES | MY USE |
|---|---|---|
| D0 | RX | serial (future: for Bluetooth) |
| D1 | TX | serial (future: for Bluetooth) |
| D2 | relay (future: to control a relay) | |
| D3 | PWM | |
| D4 | ||
| D5 | PWM | |
| D6 | PWM | |
| D7 | ||
| D8 | bit-banged I2C-SDA for T/H | |
| D9 | PWM | bit-banged I2C-SCK for T/H |
| D10 | PWM or SPI-SS | SPI-SS for SD card |
| D11 | PWM or SPI-MOSI | SPI-MOSI for SD card |
| D12 | SPI-MISO | SPI-MISO for SD card |
| D13 | LED, SPI-SCK | SPI-SCK for SD card |
| A0 | (future) keyboard | |
| A1 | ||
| A2 | ||
| A3 | ||
| A4 | SDA | I2C-SDA for RTC and LCD |
| A5 | SCK | I2C-SCK for RTC and LCD |
Software and Integration
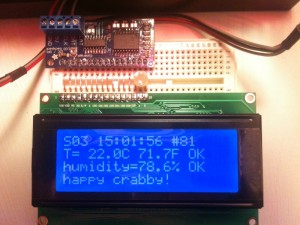
I wrote a simple program that takes a temperature and humidity reading, reads the current time, appends a line to a CSV file on the SD card, and updates the LCD display. Then it sleeps for a minute and does it all over again.
For a long while, we ran the Happy Crabby on the prototype board, with wires hanging out all over.
What we learned
We ran in this configuration for a long time. We had been thinking that we would eventually add a relay to control either a heat lamp or a terrarium heater pad. But after taking measurements for several months, we decided that temperature was nearly as much of a problem in our house as humidity.
So we kept an eye on the humidity and we rearranged the inside of the cage, dumping a few inches of moist sand into the bottom. They like to dig tunnels and hide, especially when they are molting. Overall, they seem to be healthier now that the cage is not so dry, and they are less stressed because they have a place to hide.
Almost a year after we originally started taking measurements, we decided that our design was OK enough to make “permanent”. So we bought a “shield” board and soldered all of the pieces down. I made sure that all of the pieces still plug together, in case we feel like changing it down the road. It looks a little nicer without all of the rats nest of wires, and it’s a lot less likely to get messed up if somebody bumps it.
Resources
Source code that we wrote for this project can be found on github.
We’re going to Hogwarts!
3Our family just returned from a trip to Florida.
My wife and I had been planning to take a family vacation in October during our kids’ “track out”, the three-week break between the first and second quarters of school. Since the kids (and their dad) have been reading the Harry Potter books, we thought it would be fun to visit the “Wizarding World of Harry Potter” at Universal Studios. But we did not want to tell the kids about it until we had made firm plans.
We picked our week to go, and I arranged for time off at work. And then, a week before our vacation, we got news that we would need to attend a funeral in Georgia. Rather than make that long drive twice, once for the funeral and then again the next week for our vacation, we hastily moved our vacation up a week. Since the kids still did not know about our vacation plans yet, we decided to keep it a secret. We told them to pack for the funeral, and we quietly packed an extra suitcase for them.
They were so good… stuck at a boring funeral with a bunch of boring old grownups, and yet they behaved so well.
After the funeral, a bunch of extended family went out to a restaurant. While we were there, we presented them with a mysterious letter.
It read:
Dear Misses Audrey and Sydney Porter,
We are pleased to inform you that you have been accepted at the Hogwarts School of Witchcraft and Wizardry, Orlando campus.
This special Autumn Session will take place during the week of October the 8th through the 12th. There is no need to send an Owl as we already know that you are planning to attend. All necessary materials will be provided for you.
Yours Sincerely
Minerva McGonnagall
Deputy Headmistress
So we left the restaurant and headed south for Orlando!
Although the theme of the trip was Harry Potter and Hogwarts, it was really only a small portion of our week. We spent two days at Universal Studios (one day at the Islands of Adventure and one day at the studio park), one day at Sea World, and two days at Disney World (one day at the Magic Kingdom and one day at EPCOT).
We’re going to Hogwarts!
We had a blast at all of the parks. But since the motivation behind going was to see the Harry Potter park, I want to go into a little detail about that one section of Universal Studios “Islands of Adventure” park.
I was surprised at how little of the Harry Potter theme’s potential was actually developed by Universal. For example, they have a Hogwarts Express train engine, but only as a photo backdrop. I had somehow imagined more exploration of the castle, but I suppose the parks (other than EPCOT) are not really into exploration as much as they are into moving people in a controlled manner through queues and rides. That being said, we still thoroughly enjoyed the Wizarding World experience.
The “Harry Potter and the Forbidden Journey” ride was excellent, an “experience ride” where your family-sized cart shakes and wobbles from screen to screen in a 4½ minute ride around Hogwarts. We also enjoyed the smaller roller coaster, the “Flight of the Hippogriff“, which was perfect for the average HP-reading kid (the ride was a mere 60 seconds, beginning-to-end). We chose to pass on the “Dragon Challenge“, a pretty serious-looking double roller coaster. We ate lunch at the Three Broomsticks pub and bought Butterbeer and Pumpkin Juice from a street vendor.
We also shopped at the three shops:
- Filch’s Emporium of Confiscated Goods
- Honeydukes / Zonko’s
- Ollivanders / Owl Post / Dervish and Banges
I was a little disappointed in the souvenir selections. I was kind of hoping to find a Hogwarts coffee mug… you know… all of the other dads at work have NC State and UNC mugs. But the selection was pretty lousy, so I passed. The shirts were all pretty much very expensive and tacky-looking T-shirts, nothing that I would ever wear — how about a nice golf shirt with a Hogwarts crest on it, for muggle dads? I did buy an over-priced deck of cards, but when I got home, I was disappointed to find that it contained only 14 characters from the movies, not 54. That is, the same Dumbledore picture is on all four aces, same Harry on all four kings, and so on (Fred and George are the jokers).
There were lots of Gryffindor and Slytherin items, but very few Ravenclaw or Hufflepuff items, just some crest patches, pins and lanyards. You see, lots of fans choose a favorite house to root for. It was important for us to find some Hufflepuff stuff, since at my daughter’s school, the four core teachers each lead a house, and they actually hold a sorting ceremony to assign the students to houses. But there was not much for us to choose from. (As I write this, I see that there are more items on Universal’s online store than we saw in the on-site shops, and there is more balance among the four houses).
So, we were not so tempted to part with our galleons and sickles at the shops.
The other 4½ days
The rest of Universal’s Islands of Adventure was pretty nice. The kids liked the Spider Man experience ride and the Dr Seuss area. At Universal Studios, we focused on the experience rides like The Simpsons, Men in Black and Despicable Me, and skipped the live shows (we should’ve skipped ET, considering the long wait). Sea World had some great shows, with lots of trained animals of every kind. The Disney Magic Kingdom was like visiting an old friend (October is a strange month to visit though, because at night the park transitions to a lively Halloween party, and day guests have to leave). EPCOT, as always, struck a nice balance between “rides” and “exploring”.
We had a great week in Florida, and we thoroughly enjoyed each of the parks. But both girls agree that the Universal Islands of Adventure was their favorite… because of Harry Potter, of course. Their mother preferred Sea World, and I am split between the Magic Kingdom and EPCOT.
Kingston: too scared to engage
0A while back, I ordered a couple of microSD cards from Kingston. They came with these nifty little USB card readers.
Here is a picture.
The microSD card is in the front, and there are two of the USB card readers right behind it (one is upside-down). In the back, for comparison of scale, I show a Sandisk Cruzer Micro USB stick.
These tiny little USB card readers are very nice, attractive, and very well built. You can see that the USB plug only has the inner part with the four contacts. They left off the rectangular metal shell that most USB plugs have.
The reader can be fastened to your key ring using the little nylon string that is tied into a small hole in the end. They have gone so far as to make the hole a little bit recessed, so you can still plug in the microSD card while the string is attached.
Overall, it is a beautiful design.
However, I am not a fan of the little nylon strings. I was hoping that I could use a metal fastener to attach this reader to my key chain. A metal fastener would not jiggle around or get tangled like the string would. And it would also keep the microSD card from dropping out and getting lost.
So I wrote a short note to the folks at Kingston.
Hi guys,
I am currently in the process of moving from SD cards to micro SD cards, and I just bought a few from Kingston. These came with some nice micro SD card readers (see the photo attached).
I have an idea that might make these readers better for some of your customers (and for those who do not need the change, it would be no worse than what you have now).
Your current design is just long enough so that an inserted micro SD card is flush with the back edge. You can tell that someone took some great care to design the slot where the little string goes, because it still fits when a card is inserted, and it provides a little bit of pressure against the card, to keep it from falling out.
However, if the micro SD card reader were about 1.5 mm longer, the string hole would stick out past the end of an inserted micro SD card. That is, a card could be plugged in, and you could still see through the hole. This would make it possible to use other connectors besides the little strings. Personally, I like to use small split ring keyrings. Or like I have pictured here, you could use a crab claw clasp.
The little strings are a hassle on a keyring, especially since they are holding something so light in weight. The strings sometimes get tangled up in my keys. And the string does not really ensure that the card won’t slip out… it helps by adding some friction, but it does not BLOCK the card from coming out.
It’s something to consider. I hope you will. Your little reader looks to be the tiniest and most “robust” looking of the micro card readers out there. I think this little improvement would put it way over the top as the best reader to have.
Thanks, and all the best.
Alan Porter
I was very surprised when I received a reply from Kingston.
Dear Alan,
Thank you for your interest in Kingston Technology. Also, thank you for your input and suggestion for Kingston’s product line.
Kingston greatly values our customers’ opinions and insight. Unfortunately due to today’s litigious society, Kingston is forced to discard suggestions pertaining to new and future products. Therefore, we will be unable to move forward with your input and/or suggestion. We hope you understand our position.
If you have any other questions or require further assistance, feel free to contact us directly at 800 xxx-xxxx. We are available M-F, 6am-5pm, PT. I hope this information is helpful. Thank you for selecting Kingston as your upgrade partner.
Please include your email history with your reply
Best Regards,
xxxxxx xxxxxx
Customer Service/Sales Support
Kingston Technology Company
What a nice gesture… a personal thank-you note.
But what’s this part all about??
Unfortunately due to today’s litigious society, Kingston is forced to discard suggestions pertaining to new and future products.
I was shocked. They thanked me for writing, but they simply won’t allow themselves to listen to their biggest fans, because they’re scared that someone might sue them for listening.
What a horrible statement about our society! This is the exact polar opposite of the principles of sharing and feedback and continuous improvement that I am used to dealing with in the open source community.
Kingston lives in a feedback-free vacuum, fingers in their ears, and they blame us all for their uncooperative attitude. What does this say about us? Has the greatest nation in the world slowly grown old and senile, becoming scared of its own shadow? Will my children grow up to be scared to talk to strangers, scared to have a genuine dialog with another human, scared to actually accept criticism and suggestions, scared that someone would sue them, scared that they might tarnish their sacred brand? Is this the world that I want to leave to my children? Hell, no. So I made sure to write back to Kingston and register my disapproval of their spineless policy.
I hope some Chinese company will run with the elongation improvement. They don’t seem to be crippled by the imaginary legal threats from their own customers like Kingston seems to be.
I should note:
- I still like Kingston and their products. But this extreme risk aversion is the wrong way to go.
- My “improvement” has now been published (here on this blog), and so it is now officially “prior art” and can not be patented. That means that companies — Kingston included — are free to use this idea without fear of being hit up on charges of patent infringement.
- The newer business tactic is to actively engage customers, creating a dialog with them, and letting them feel like they are contributing; not to blow them off and blame it on society.
Personally, I hope we will begin to see less of this corporate (and personal) scaredy cat culture in America.
Garage Door Monitor
3How many times have I gone outside in the morning, only to find that I had left my garage door open all night? Too many. I hate that uneasy feeling that I have just invited thieves into the garage for some easy pickin’s (truth be told, I’d be happy if they took some of that junk, but still).
For a long time, I had thought of rigging up a light upstairs that would come on whenever the garage door was open. That way, at night, it would be pretty obvious that I had left the door open. But I let that idea sit dormant for a long time.
Then I read an article in Make magazine (“12,000-Mile Universal Remote“, issue 30, page 66). In it, the author built a board called an “XBee Pulse I/O” that watched a door sensor, tapped the opener’s switch, and communicated with an XBee internet gateway. These talked to a cloud service called iDigi. This was not exactly what I wanted to do, but it pushed me in the direction I needed.
I decided that I wanted to build an Arduino board that would monitor my garage door. I wanted it to communicate with my home Linux server, “Bender”, which I consider to be sort of a digital butler, keeping track of stuff around the house and reminding me of stuff that I need to know.
PONDERING WIRELESS SOLUTIONS
For the next few weeks, I pondered how I would hook the Arduino board in the garage to Bender, which lives in the bonus room over the garage. I was not too fond of the idea of running a wire, even though the distance is very short. I scoured the internet for ZigBee boards, but soon decided that these were very pricey for what they did.
Inside the garage, I would need an “XBee” ZigBee radio module, which costs about $24~$40. But I would also need a controller board for another $10. This controller board acts as a front-end, providing a simple serial port to my project, and taking care of all of the ZigBee protocol stuff.
Then, on Bender’s end, I would need a similar XBee module ($24) and a USB adaptor ($20).
That’s a total of $78~$110, just for the wireless link!
Surely, dropping a Ben Franklin down for a home project is not such a big deal. But I was concerned that as my project grew, I might be adding many wireless links to it. And at $50 a pop, I figured it would be worthwhile to broaden my search a bit.
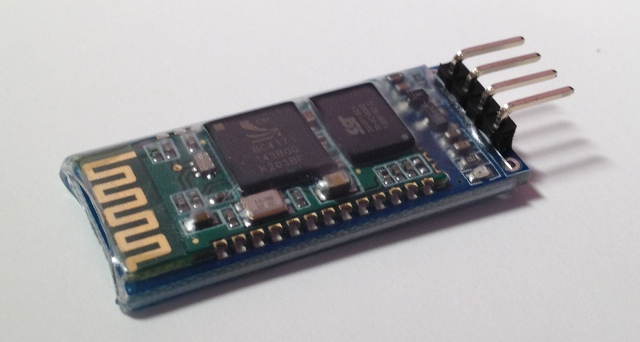
WHAT ABOUT BLUETOOTH?
I worked for Ericsson from 1998 until 2003, when they were first developing the Bluetooth standard. I remember reading presentations about the technology before they had come up with the Bluetooth name… internally they referred to it as “MC Link”, and occasionally, (my favorite) “wireless wire”! I knew that the goal for Bluetooth was to make these communication chips so low-power and so cheap that every device would include one… WORLD DOMINATION!
With that in mind, I wondered whether there were simple Bluetooth serial communication boards that would work with an Arduino. I found one, called the “BT2S” from Virtuabotix. It was only $15, and it looked pretty easy to use. AND… I would only need ONE on the garage monitor side, because I could use Bender’s existing Bluetooth interface!
I ordered two BT2S sticks from Virtuabotix. Later, I found another source for almost-identical boards. DealExtreme has the JY-MCU Arduino Bluetooth Wireless Serial Port Module for $8.60! (Be careful not to get the TTL version that looks very similar).
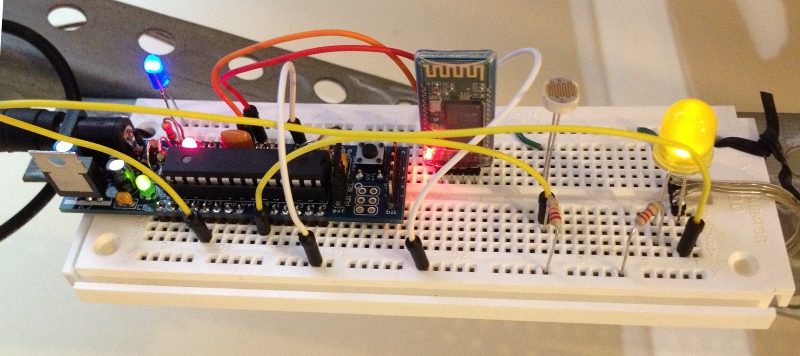
PUTTING IT TOGETHER – THE HARDWARE
I am not too fond of crawling up a ladder to reprogram my Arduino in my garage, so I decided to make the Arduino end of this project as simple and generic as possible.
The BT2S module plugs in to the Arduino’s serial port, and the program on the Arduino simply listens for serial commands and responds. I decided to implement three commands: read digital, write digital and read analog. That way, nothing would be hard-coded into the Arduino. Instead, all of the smarts would be in the client program that runs on Bender.
I plugged in a magnetic reed switch to one of the digital inputs, and an LED to a digital output. While I was at it, I put a light sensor on one of the analog inputs.
Then I hung it up on the garage door frame. I stuck a very strong hard drive magnet on the door so it would be close to the reed switch whenever the door was open.
TALKING TO IT VIA BLUETOOTH
Bender is a Linux machine, and so I needed a Linux-based program that would open a Bluetooth serial connection to the Arduino and then send serial commands to it. I needed a mixture of shell commands to configure the Bluetooth connection and low-level communication to the serial port. So I chose Python.
Bluetooth is a complex protocol that supports a lot of different uses: real-time audio, serial communication, keyboard/mouse, dial-up networking, and more. We’re using a simple serial link, which they call “rfcomm”. In Linux, we establish the serial link using the rfcomm command. It makes a Bluetooth connection to the device and creates a serial port device named /dev/rfcomm0.
Once we have created a serial device, the python program simply reads and writes to that device just like any other file. I structured my program as a big loop with timers. Every so-many seconds, it sends a command to read the magnetic reed switch. It also sends commands to blink the LED, so I can tell from the garage that the python program is still running. When the reed switch response comes back, it writes the door status to a file. If I put that file in an area that is shared via my web server (/var/www/ or $HOME/public_html/), I can check on my door from any browser.
If the door state has changed since the last time it was read, the python program sends a push notification (like a text message) to my phone. This is another idea that I stole from the same issue of Make magazine (“You’ve Got (Snail) Mail“, page 76). This uses an iPhone app called “Prowl” and a web service that goes along with it.
COMPLETING THE LOOP
Sure, it’s cool to hear my phone “bling” when someone opens the door at home. But my original motivation was to be warned when I had left the door open.
Fortunately, that’s an easy job. I wrote a simple “cron” job that reads that status file at certain times of day (or night). If the door is open, it sends me another push notification saying “hey dummy, your garage door is still open!”.
RESOURCES
Source code and other resources can be found on github.
CarolinaCon 8
2Once again, it’s time for a weekend of frivolity and technology that we call “CarolinaCon”. While I was sure that doing so would put me on some secret list of persons-to-watch, I made plans to attend.
As usual, the Con spanned the weekend, from Friday evening until Sunday evening. Here’s my impressions.
FRIDAY EVENING
- 7:00pm – Identifying Cyber Warriors (Tom Holt / Professor Farnsworth)
The professor always does such a good job of easing the crowd out of reality and into the “Con-zone”. His presentations are academic, but touch on hacker culture. This year, he gave questionnaires to college students to determine correlations between their attitudes on protesting and hactivism across two dimensions: domestic-vs-foreign and physical-vs-virtual. - 8:00pm – Bypassing Android Permissions (Georgia Weidman)
Georgia explained how Android phone apps implement “intents” or services, and then how to inspect an Android app to see its contents. Using these two pieces, she was able to write unprivileged apps that use another app’s higher-priviledge services. - 9:00pm – Intro to Hacking Bluetooth (ronin)
Ronin has assembled a wide array of open source Bluetooth tools into a Linux distribution that he calls “Blubuntu”. He showed the basic usage of some of these tools, with some good background info on how the protocols work. A good overview talk! - 10:00pm – F-ing the Friendly Skies (Deviant Ollam)
The original plan was to end the Friday night session with a round of Hacker Trivia, but the schedule was abruptly changed to include this entertaining talk from Deviant Ollam, whose talks usually center on lock picking and air travel (and they usually include alcohol). This year’s presentation did not disappoint — the topic was the “Mile High Club”, with a complete survey of logistics, opportunity, and suggestions for flight timings and choice of aircraft.
SATURDAY
- 10:00am – DevHack: Pre-Product Exploitation (Snide)
Once they cranked up the volume on Snide’s mic, he walked us through several ideas for planting malware into a software development environment, implanting your payload at the source. - 11:00am – Malware Retooled (Big-O)
This talk discussed how we can watch what malware DOES rather than trying to match against signatures. Big-O showed some nice visualization tools, like thread graphs. - lunch break
- 1:00pm – Inside Jobs: Stealing Sensitive Data and Intellectual Property (Vic Vandal and emwav)
Vic and emwav enumerated several ways that companies and employees can escalate the arms race… employees can steal proprietary information, and employers can make it difficult. The bottom line for me was that this arms race is stacked in favor of the attacker. - 2:00pm – Project Byzantium: Improvisable Ad-Hoc Wireless Mesh Networking for Disaster Zones (Sitwon The Pirate and The Doctor)
Apparently, someone told this group that CarolinaCon was a costume party. The pirate and the doctor win the prize for best costumes. But pay closer attention. These guys are smart — they have scoured the internet for cool mesh networking tools, and they have packaged them into a LiveCD distro called “Byzantium”. Imagine a disaster or political unrest scenario, where you would like to mesh together a group of users and share an internet connection. Keep an eye on this fledgling project. - 3:00pm – Hacking as an Act of War (G. Mark Hardy)
Gmark has been keeping his eye on the geopolitical landscape and how different nations approach info security. He has insights into the capabilities and motivations of the different players, and he observes recent cyber-attacks that have shaped the new balance of powers. Where do we draw the line between hacking and warfare? - 4:00pm – Big Bang Theory: The Evolution of Pentesting High Security Environments (Joe McCray)
Joe warns corporate America that we should stop focusing on the vulnerabilities, stop patting ourselves on the back when we’ve checked all of the patch check boxes, and instead focus on why an attacker would be interested in their companies to begin with, and prioritize based on the value of the assets (illustrated with a colorful analogy about driving through the ‘hood). - Dinner Break
- 7:00pm – Spyometrics: New World of Biometric Surveillance (Dr. Noah Schiffman, aka Lo-Res)
This talk had a lot of promise, because the subject matter is wide open for thought-provoking stories. But I felt like this talk left more loose ends than tied-up ones. - 8:00pm – Dr. Tran goes to Switzerland (Dr. Tran)
One of the best talks of the show, and it was not even about security! Dr Tran recently moved to Zurich, and he recorded his impressions and shared them with the Con attendees. - 9:00pm – Hacker Trivia
Much like hacker trivia in previous years, but I noticed three differences. The game was more lightly attended than at previous cons. Many of the questions went unanswered (meaning Vic had to take a drink). And most disappointing, Al did not emcee.
SUNDAY
- 10:00am – Attacking CAPTCHAs (Gursev Singh Kalra)
This talk was canceled. Instead, we heard from some UNC-Charlotte students on the accomplishments of their hacking competition team. - 11:00am – Patch to Pwned: Exploiting Firmware Patching to Compromise MFP Devices (Deral Heiland)
Deral Heiland has made a career out of keeping printer manufacturers on their toes. This time, he decomposes a firmware update package for Xerox printers, and he creates his own update that includes his “modifications”. - Lunch Break
- 1:00pm – Hacking your Mind and Emotions (Branson Matheson)
Branson shows how easily we can be socially engineered. It happens every day, from advertisers, authority figures and administrators. He shows us how to recognize when we’re being manipulated, and he encourages us to know our rights and responsibilities so we can limit our exposure. - 2:00pm – It’s 2012 and My Network Got Hacked (Omar Santos)
Case studies of real-life compromises, in spite of the sophisticated defenses employed. Omar discussed the challenges that are encountered by large organizations with wide networks and hundreds of assets to manage. - 3:00pm – Declarative Web Security: DEP for the Web (Steve Pinkham)
Modern browsers are starting to include advanced policy engines that allow web sites to declare rules, such as “only run javascript from this host”, in an attempt to restrict what potential malware can do. - 4:00pm – Raspberry Pi’s Impact on Hacking (DJ Palombo)
OK, the RaspPi is a cheap small computer. We get that. DJ Palombo seems to think that the revolutionary concept is that its low profile and disposability make it a good “bug” or or hidden node for hacking.
Thanks to the organizers and presenters for another memorable Con!
‘sudo’ vs using a root password
0There seems to be a lot of confusion about the use of “sudo” vs using a root password. It’s a lot simpler than many make it out to be.
- On a system that uses a root password, all administrators use a shared root password.
- On a system that uses “sudo”, all administrators use their own passwords.
- There is no reason why you can’t do both.
Some people argue about a Linux distribution’s default setting, when they could simply change the setting after installation and forget about it.
- To enable a root password:
$ sudo passwd root - To disable a root password:
$ sudo passwd -l root - To start using sudo:
# apt-get install sudo
# adduser username sudo - To stop using sudo:
# gpasswd -d username sudo(optional)
# apt-get remove --purge sudo - To run a “su-like” shell using “sudo”:
$ sudo -s(runs a normal shell)
or
$ sudo -i(runs a login shell)
Personally, I have gotten used to disabling my root password and the using either sudo -i or ssh root@hostname. That’s one less password for me to remember, and one less password that can be probed on the network.
But you don’t have to be like me… you do what feels right to you!
Debian’s “dist-upgrade”
1There seems to be a common misconception about Debian’s package manager “apt”, that the command “dist-upgrade” is used to upgrade to a new release. It is, but it isn’t. I wanted to clarify that here.
Basically, there are 4 things that you might want to do as part of upgrading a system.
apt-get update– updates the list of available packages and versionsapt-get upgrade– upgrade packages that you already haveapt-get dist-upgrade– upgrade packages that you already have, PLUS install any new dependencies that have come up- edit the sources files – change the release that you are tracking
That means that to freshen up your packages to the latest versions on your current release, you should do “apt-get update && apt-get dist-upgrade“. On some systems that track “testing”, which changes often, I do this almost daily.
When you’re ready to “really upgrade” to a new release, you edit your sources files in /etc/apt/sources and change the release names. If the source lists contain proper release names, like “etch”, “lenny”, “squeeze” or “wheezy”; then you change these names to the new release that you want (see http://www.debian.org/releases/). If the source lists contain symbolic names like “stable”, “testing” and “unstable”, you do not need to change anything. When a new release is ready, the Debian people will change the symbols to point to the new release names. For example, right now, stable=squeeze and testing=wheezy.
Note 1 – “unstable” never points to a named release… it’s the pre-release proving ground for packages, used before are ready for inclusion in the testing release.
Note 2 – Don’t let these symbolic names fool you:
- “Stable” means “old, tried, tested, and rock solid”. It’s a very conservative choice.
- “Testing” does not mean “chaotic”. It is roughly the equivalent of Red Hat’s Fedora. It’s new stuff, and each package changes on its own schedule, but they usually play well together.
- “Unstable” is not nearly as unstable as the name implies. It’s like a beta release that may be updated daily.
After your source lists look OK, you do the same thing you’ve always done: “apt-get update && apt-get dist-upgrade“”apt-get update && apt-get dist-upgrade“.
If you’re running Ubuntu, the release names are at http://releases.ubuntu.com/. And they’ve made a nice wrapper script called “do-release-upgrade” that basically edits your source lists and does the dist-upgrade for you (it also does some other nice steps, like letting you review the changes).
So there it is… fear not the “dist-upgrade”. In fact, most of the time, it is what you’ll want to run. It will make sure that you have all of the dependencies that you need.
Host your own calendar server – iPhone client
0I am a bit of a do-it-yourselfer. When looking for a new service like an online photo gallery, my first instinct is to find an open source package where I can host photos on my own web server. I know that many will skip this step and go directly to Picasa.
These days, it seems to come down to those choices: do it yourself, or give another slice of your life to Google. In this post, we’re going to do it ourselves.
Ever since the days of the Palm Pilot, I have made heavy use of the calendar application. When I switched to the iphone in 2009, I decided that I wanted to use a online calendar that I could access from my laptop and from the iphone. I looked at the open source world, and I found a package called DavICal, by Andrew McMillan in New Zealand. It uses the CalDAV protocol to exchange event information with clients like the iphone’s calendar, iCal on the Mac, Mozilla Thunderbird with the Lightning plug-in, Mozilla Sunbird, and (I think) Outlook.
Setting up the server is pretty well documented on the DavICal web site. On a Debian-based server, it’s a simple “apt-get” operation (after you add their site to your sources list).
Below, I will talk about how my calendars are organized, and then I’ll walk through the steps of setting up a new user and calendars on the server, and then setting up the iphone to access these new calendars.
How I organize my calendars
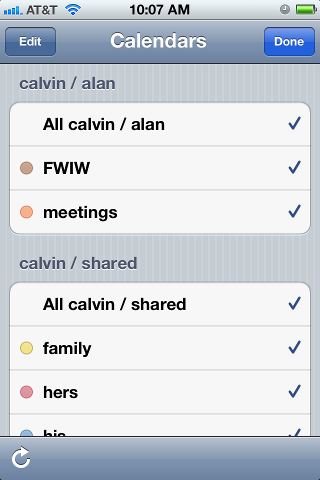
I organized my calendars in two groups, owned by users “alan” and “shared”. The “alan” user owns a set of calendars that I use, but that my family does not care about. The “shared” user is stuff that we all need to see. This might seem a little weird, but it makes things work out well on the iphone. Below is a picture of the iphone’s “calendars” screen, which shows this grouping. Notice the orange calendar called “meetings”. I have meetings at work all day, and my wife really doesn’t need to see them on her ipod, and she does not need to hear the reminders throughout the day. So the meetings calendar is owned by the “alan” user. On the other hand, we all need to know about family events (yellow), “his” stuff (blue) and “her” stuff (red). That stuff is owned by the “shared” user.
Below, when we set up the iphone calendar accounts, I will have two accounts (“alan” and “shared”), and my wife will only have one (“shared”). I am sure there are other ways to get the permissions to work out, but this is dead-simple, and it shows the division in the screen shot below.
In case you wondered, “calvin” is my server. And “FWIW” stands for “for what it’s worth”… stuff that I want to know about, but that I am not planning on attending. I want to know when Mardi Gras and Burning Man and DefCon are taking place, but I am not going to any of them.
On the server
We’ll start with the DavICal web interface, which is functional, but not very polished. You need a user account, and that user can own several calendars (called “collections”).
To create a user on the DavICal web interface, you need to log in as an administrator and use the menu to “create a principle” of type “person”. See? Precise, carefully worded, but not so user-friendly.
The new user can now add calendars by logging into the same web interface and selecting “User Functions” and “List My Details”. That screen shows a bunch of junk you don’t care about at the top. But at the bottom, there is a list of “collections”. That’s the CalDAV term for a calendar. Use the “Create Collection” button to make one or more calendars. Make sure to give them a “display name”. That’s the name that will show up in the iphone’s calendar list.
On the iphone
Once you have the calendars on the web system, the iphone part is easy. Go to “Settings”, “Mail, contacts, calendar”, and “add account” of type “other”. Select “CalDAV”. Enter four things:
Server=(the nostname of your CalDAV server) Username=(your new user's name) Password=(your password) Description=(some name)
When you hit “next”, it may pop up a box complaining about SSL certificates. In my case, I don’t have proper SSL certificates, so we’re going to just say “continue”. Setting up SSL on the server is a future blog post. So we’ll say “continue”. At this point, you wait… and wait… for the iphone to guess all of the rest of the settings it can think of.
It will finally finish, and you’ll have to again tell it “don’t use SSL”. But surprisingly, it should have figured out the rest of the settings.
SSL=off port=80 URL=http://USER@SERVER/caldav.php/USER
At that point, when you open the iphone’s calendar application, your server should show up in the calendar list, with all of the individual calendar names below it.